UXLINK Hack Explained: AMLBot On-Chain Analysis Reveals a Possible Staged Phishing Twist
The hacker got hacked. But was it real? Dive into our on-chain breakdown of the UXLINK exploit and its tangled money trail.

On-chain evidence shows the UXLINK hack stemmed from a delegateCall-based admin takeover; stolen funds were rapidly laundered across chains, the token crashed 70%+, and the later “hacker got phished” episode may have been staged to obscure the money trail.
On September 22, 2025, the Web3 social platform UXLINK suffered a significant security breach, sending shockwaves through the DeFi community.
Attackers exploited a vulnerability in UXLINK’s multi-signature wallet smart contract, gaining administrative control and draining millions of dollars in cryptocurrency. The incident not only led to unauthorized minting of billions of UXLINK tokens and a sudden 70%+ collapse in the token’s price, but in a strange turn of events, the hacker themselves later fell victim to a phishing scam.
Below, we break down how this exploit, the immediate market fallout, UXLINK’s response with a token swap plan, and how ongoing investigations are tracing the stolen funds to prevent further damage.
From DelegateCall Exploit to Complete Admin Takeover
Security analysts quickly identified the root cause of the hack. A flaw related to a delegateCall function in UXLINK’s Ethereum and Arbitrum smart contracts. This error allowed the attacker to execute an arbitrary delegate call, effectively granting themselves admin rights over the UXLINK multi-sig wallet. In a swift on-chain sequence, the hacker stripped the real owners of their privileges and added their own address as the wallet’s owner. With full control acquired, the perpetrator systematically withdrew assets and inflated the token supply:
(а) Stablecoins & ETH: Approximately $4,000,000 USDT, $500,000 USDC, 3.7 WBTC, and 25 ETH were transferred out of UXLINK reserves.
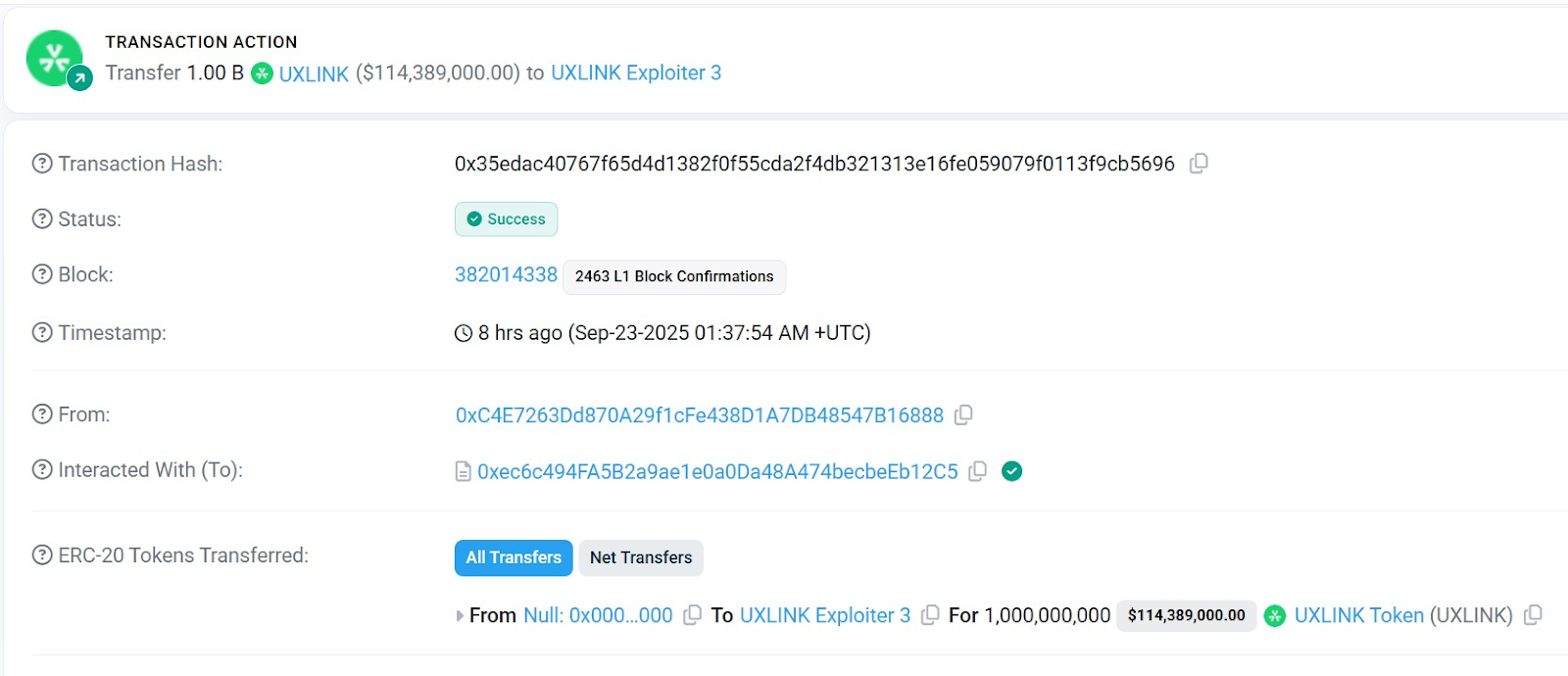
(b) Native Tokens: The attacker seized ~490 million existing UXLINK tokens from the treasury and then minted an additional 1–2 billion UXLINK via the compromised contract. This nearly doubled the total supply, expanding it from ~995 million to nearly 2 billion tokens in just a matter of minutes.
(c) Converted Loot: Moving quickly across at least six different wallets, the attacker swapped the stolen assets into other cryptocurrencies, primarily converting large portions to ETH. In total, they netted approximately 6,732 ETH (about $28.1 million) by dumping tokens on both centralized and decentralized exchanges. On Ethereum, stolen stablecoins were also swapped into DAI, and some funds on Arbitrum were converted to ETH and then bridged back to the main Ethereum network to consolidate the haul. At least $800,000 worth of UXLINK was dumped within hours of the breach, causing immediate sell pressure and foreshadowing a broader panic.
UXLINK Token Price Analysis
As news of the attack spread and the attacker’s massive token dumps hit the market, UXLINK’s price plummeted. Within hours, the token collapsed by over 70%, plunging from around $0.30 to under $0.10. In intraday trading, the drop was even deeper, at one point exceeding 90% (from approximately $0.33 down to approximately $0.033) before a partial recovery.
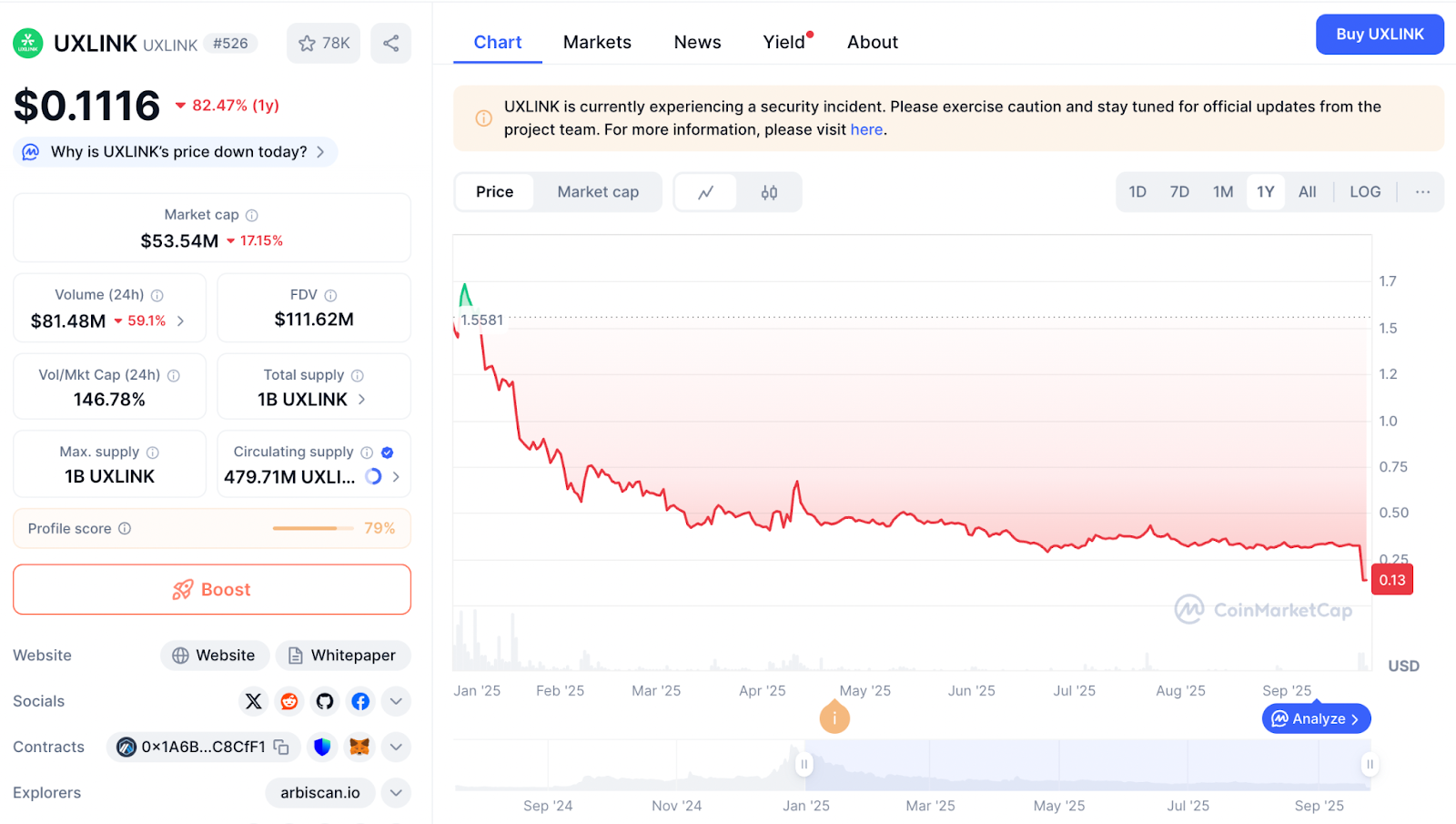
Other assets also felt ripple effects. ETH’s price came under pressure in the aftermath, likely because the hacker was converting stolen tokens into ETH and cashing out, adding sell pressure to an already fragile crypto market.
By mid-2025, UXLink had claimed over 54 million registered users globally. UXLINK had been considered a rising success story in the Web3 space. The sight of its token in free fall, with over three-quarters of its value erased in hours, shook user confidence and sparked debates on security across the DeFi sector.
Several major crypto exchanges responded by halting UXLINK token deposits and withdrawals to prevent the hacker from offloading more stolen tokens on their platforms. For example, Upbit and other exchanges collectively froze an estimated $5–7 million linked to the suspicious addresses within the first day.
UXLINK’s team publicly acknowledged the breach about six hours after the exploit, confirming that unauthorized tokens had been minted and reserves drained. They immediately reached out to both centralized exchanges and decentralized exchanges, requesting that they freeze any suspicious deposits of UXLINK or related funds. By the following day, UXLINK reported that “a large portion of the stolen assets has already been frozen” thanks to coordinated action with exchanges.
Token Swap Plan and Security Overhauls
In the wake of the attack, UXLINK’s priority shifted to stabilizing the project and planning a recovery. One of the core challenges was the flood of illegitimately minted tokens now in circulation. UXLINK announced an imminent token swap and contract upgrade designed to restore the token’s integrity: all legitimate UXLINK holdings would be swapped 1:1 into a new token, while the billions of fraudulently minted tokens would be excluded and effectively destroyed. By transitioning to a new smart contract with a fixed supply cap, the project aimed to prevent any further unauthorized minting from occurring.
As of the latest updates, UXLINK’s developers have submitted the new contract for a security audit and are finalizing the swap implementation. Users have been advised to refrain from trading the existing UXLINK token until the migration is complete and to follow only official channels for instructions on swapping tokens safely.
Beyond the token swap, UXLINK is taking additional steps to enhance its security and rebuild trust. Notably, the original contract lacked a hardcoded supply cap on token minting and had inadequate access control protections, which made the delegateCall exploit catastrophic. In hindsight, basic safeguards such as time locks on critical administrative functions or an emergency pause could have slowed or stopped the attacker’s actions, buying time for intervention.
UXLINK’s team, in collaboration with blockchain security experts, is reviewing these vulnerabilities to prevent a repeat incident. They have indicated plans to implement more robust multi-layer key management, stricter admin privileges, and perhaps community oversight over any future contract changes. Exchanges such as Upbit and Bithumb have also taken precautions by flagging UXLINK as a high-risk asset for the time being. In one case, they have labeled it a “cautionary asset” under their user protection frameworks.
Hacker Becomes a Victim of Phishing
As if the initial exploit weren’t dramatic enough, the UXLINK incident took a comical turn within 24 hours. While investigators and the community scrambled to track the stolen funds, on-chain data revealed that the UXLINK hacker had fallen prey to a phishing scam and lost a significant portion of their ill-gotten tokens. In what many in the crypto community described as a dose of “instant karma,” the attacker was tricked by a second malicious actor into signing away their own tokens.
According to analyses by security researchers, the hacker unwittingly approved a malicious smart contract, which allowed a phishing wallet to siphon away about 542 million UXLINK tokens from the hacker’s address. Those stolen tokens, valued at roughly $48 million at the time, were traced to the notorious Inferno Drainer phishing group, which has been linked to numerous scams.
The thief got robbed by another thief. No one is immune to cybercrime. Not even other cybercriminals. But, most importantly, this incident did not undo the damage to UXLINK or refund users' funds. In fact, the incident highlights how chaotic post-exploit flows can be: stolen assets may ricochet between criminals, get subdivided, or be lost in secondary scams, making recovery even more challenging.
Ongoing Investigation and AMLBot’s Monitoring of Stolen Funds
In the aftermath, UXLINK has been working closely with law enforcement and blockchain forensics teams to track the movement of the stolen funds. A significant portion of the loot remains at large. Analysts estimate that between $20–30 million in assets are still under the primary hacker’s control, sitting in various addresses that haven’t been fully off-loaded.
AMLBot has been actively involved in tracing these funds. Using on-chain investigation techniques, our team mapped out the attacker’s wallet addresses and fund flows. From the initial exploit transactions to the swaps and bridges used to launder the proceeds. For example, it was observed that the exploiter’s main address swapped large amounts of USDT for ETH on Arbitrum and then bridged those ETH to the Ethereum Mainnet.
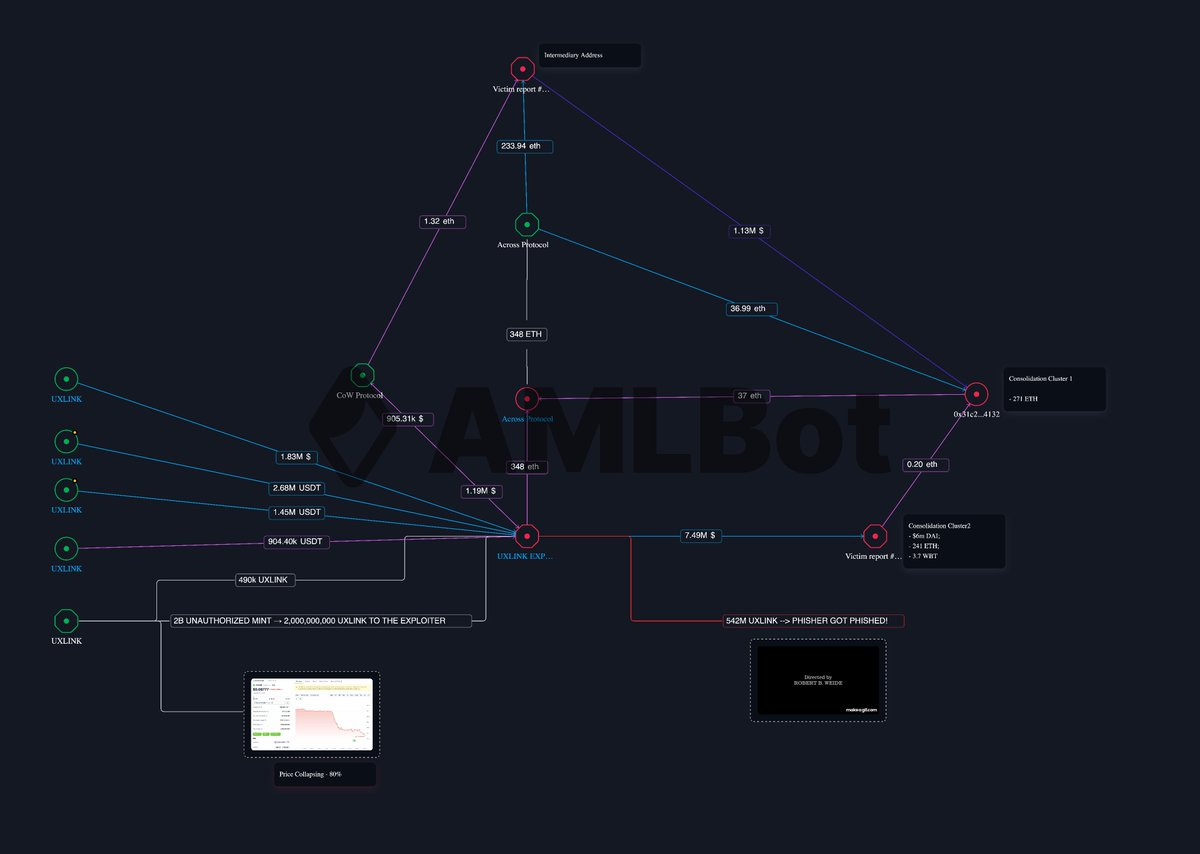
By following the trails of these transactions, AMLBot and other investigators can identify exchanges or DeFi platforms where the thief moved assets, and work with those services to flag or freeze the illicit funds.
We also suggest that there is another possible scenario. It cannot be ruled out that the supposed “hack of the hacker” was not an accident at all, but a carefully staged maneuver. From our perspective, it may have been a move to make the situation appear even more chaotic and thereby simplify the laundering process.
And in fact, there are several reasons why this scenario makes sense. Firstly, false-flag tactics are nothing new in cyber operations. Pretending to be a victim can easily throw investigators off balance and buy the attacker more time. Then there’s the convenient excuse: “I was phished.” In crypto crime, this has almost become a cliché, especially with Drainer-as-a-Service schemes making it hard to distinguish one actor from another. On top of that, for exchanges and law enforcement, such a move creates triage overload. They suddenly have to deal not only with the original exploit but also with a supposed secondary hack, which fragments workflows and slows down the entire response. And finally, there’s precedent. We’ve already seen projects and even insiders reframe rug pulls as hacks to avoid accountability. It’s a different angle, but the same old playbook: twist the narrative just enough to confuse everyone and regain control.
However, whether real or staged, the effect is the same: the more tangled and confusing the situation becomes, the harder it is to separate fact from deception. And in practice, it remains unknown what further measures malicious actors might resort to just to cover their tracks and keep investigators chasing shadows.
–AMLBot Investigation Team
Contact AMLBot’s Crypto Recovery Team for an expert on-chain investigation.
FAQ
What Did the On-Chain Data Reveal About the UXLINK Exploit?
On-chain evidence confirmed that the exploit came from a vulnerability in UXLINK’s multi-signature smart contract using the delegateCall function. This flaw allowed the attacker to seize full admin control, mint billions of new UXLINK tokens, and drain millions in stablecoins and ETH. Transaction tracing also showed how the hacker moved and swapped stolen assets across multiple wallets and chains to conceal their origin.
Were the Stolen Funds Successfully Traced?
Yes — AMLBot analysts and other blockchain investigators traced the main flow of stolen funds. Roughly $20–30 million remains under the primary hacker’s control, while several exchanges froze suspicious deposits worth $5–7 million soon after the breach. On-chain maps reveal detailed paths through which the hacker converted USDT and USDC into ETH and bridged them between Arbitrum and Ethereum Mainnet.
Could the Hacker’s Wallet Breach Have Been Intentionally Staged?
It’s possible. While initial reports suggested the hacker later became a victim of phishing, AMLBot’s investigation team proposes another explanation — that the “phish” was staged deliberately to mislead investigators and slow the recovery process. Such false-flag tactics are common in crypto exploits, helping attackers disguise laundering steps and fragment the investigation trail.
