$13.5M Lost in Aperture Finance & SwapNet Exploit: Full On-Chain Breakdown

Date: February 3, 2026
Incident Type: Smart-Contract Exploit (Unlimited Approval)
Total Losses: ~$13,500,000+
In late January 2026, the DeFi ecosystem was rocked by a series of linked exploits targeting Aperture Finance and 0xswapnet. Despite serving different niches, both protocols fell victim to the same critical architectural flaw: the improper handling of unlimited token approvals.
The AMLBot team, utilizing our blockchain analytics tool Tracer, has conducted a comprehensive forensic analysis of the fund flows. Our findings reveal a sophisticated laundering operation and a direct link to the notorious Li.Fi attacker network.
Aperture Hack: On-Chain Tracing Connects Exploit to https://t.co/ipnSUAr103 Attacker Network⁰
— AMLBot (@AMLBotHQ) January 27, 2026
Both @ApertureFinance and @0xswapnet contracts were exploited due to unlimited token approvals. So far, only Aperture Finance has publicly acknowledged the vulnerability and has already… pic.twitter.com/l8hDnivvOj
Stay in the Loop: Follow Us on X for Quick Updates: @AMLBotHQ
The Anatomy of the Exploit
The breach centered on an "arbitrary call" vulnerability. Attackers manipulated contract functions to trigger unauthorized transferFrom operations. Essentially, any user who had previously granted these protocols "infinite approval" for their tokens had their balances siphoned directly into the attacker’s control.
While Aperture Finance has proactively acknowledged the vulnerability and initiated on-chain communication with the perpetrator, the scale of the drain across both platforms remains significant.
On-Chain Overview via AMLBot Tracer
Using Tracer, we mapped the primary flow of stolen assets, beginning with the attacker's main hub on the Base network:
Main Attacker Address: 0x6cAad74121bF602e71386505A4687f310e0D833e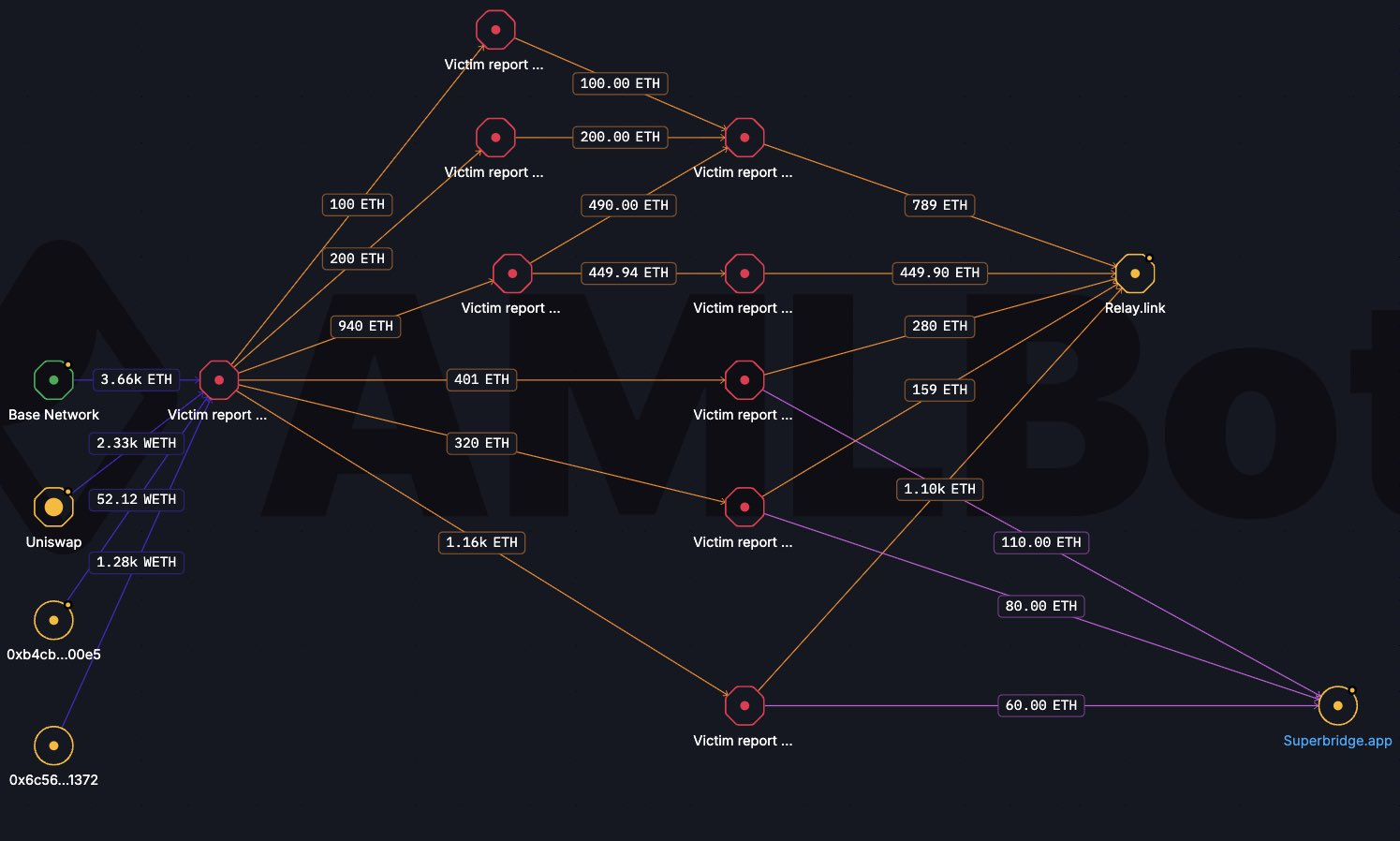
Phase 1: Consolidation and Conversion
The attacker successfully extracted approximately $13 million in various assets:
- ~$3M USDC remains untouched on the original Base address, likely due to liquidity monitoring or potential freezing risks.
- The remaining alt-assets were swiftly swapped into ETH.
- Currently, ~540 ETH is being held at the primary entry point.
Phase 2: Cross-Chain Laundering Pattern
The perpetrator employed a professional-grade laundering route to obfuscate the paper trail. Funds were moved from Base to Ethereum Mainnet using high-throughput bridging protocols: Relay Protocol/ Superbridge.
Once the funds reached Ethereum, they were dispersed across a network of fresh intermediary wallets. Interestingly, these wallets are currently dormant, though they have become targets for address poisoning attempts by third-party scammers hoping to capitalize on the high balances.
The "Copycat" and the Li.Fi Connection
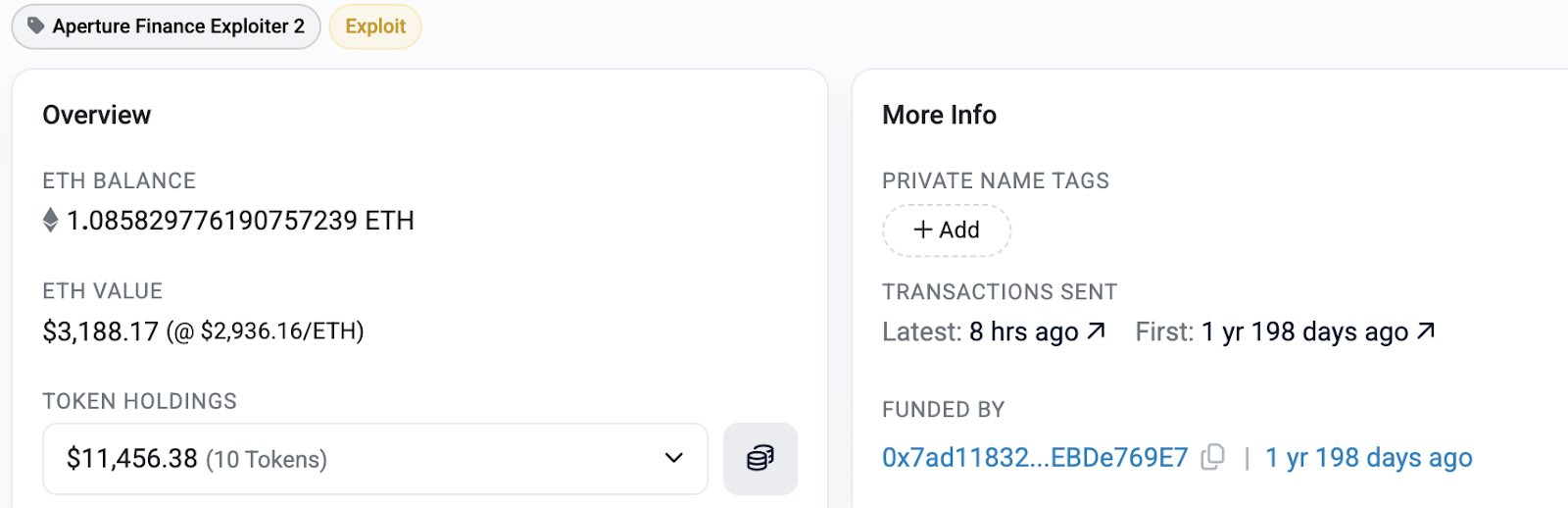
Our clustering analysis identified a second, distinct wave of activity occurring hours after the initial exploit. This "copycat" attacker focused on Aperture Finance specifically, holding funds at:
0xe3E73f1E6acE2B27891D41369919e8F57129e8eA(~$3.2M)0x5FF8645BbC6c8B4390aA228A3e8bf08240F333b4(~$15K)
Our tracing shows that the second address was funded via Tornado Cash over a year ago. Most importantly, our database links this specific wallet cluster to the Li.Fi Protocol / Jumper Exchange attacker.
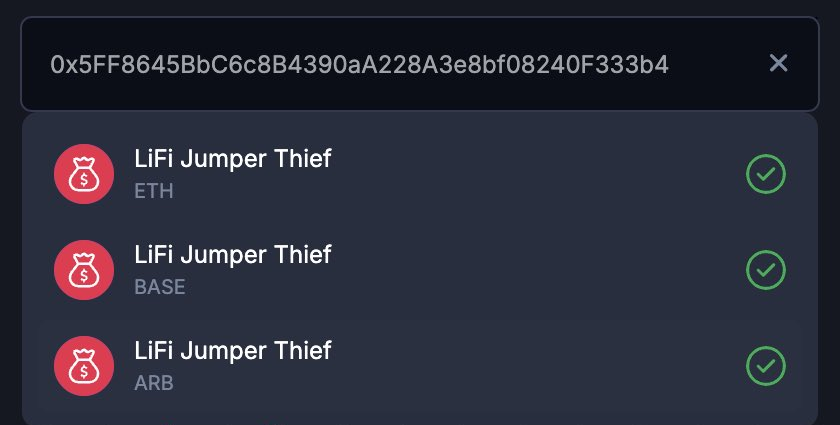
This suggests that the Aperture exploit was not just a one-off hit but was picked up by a sophisticated threat actor group that specializes in "infinite approval" vulnerabilities.
What This Means
This incident serves as a reminder of the "toxic legacy" of infinite approvals. Even if a protocol is audited or reputable, a single unvalidated low-level call can turn a user's approval into a backdoor for drainers. AMLBot continues to monitor all associated wallets.
-AMLBot Team

Follow AMLBot:
🔗 Website
🔗 Telegram
🔗 Support Team
🔗 LinkedIn
1. What Happened To Aperture Finance And SwapNet?
In late January 2026, both Aperture Finance and SwapNet were exploited due to a critical smart contract vulnerability. Attackers leveraged an arbitrary call flaw, allowing them to drain funds from users who had granted the protocols infinite token approvals.
2. How Much Was Stolen In The Aperture Finance Hack?
Based on on-chain data traced by AMLBot, the combined losses across both protocols exceed $13.5 million. The majority of the funds were stolen in USDC and ETH, with a significant portion being bridged from the Base network to Ethereum Mainnet.
3. Is There A Link Between The Aperture Exploiter And The Li.Fi Hack?
Yes. Our clustering analysis identified a "copycat" attacker whose wallet was funded via Tornado Cash over a year ago. On-chain forensics link this address to the same entity responsible for the previous Li.Fi Protocol / Jumper Exchange exploits, suggesting a recurring threat actor group.
4. How Did The Attackers Launder The Stolen Crypto?
The attackers followed a professional cross-chain laundering pattern. They used Relay Protocol and Superbridge to move ETH from the Base network to Ethereum. The funds were then dispersed across multiple dormant intermediary wallets to avoid detection by automated AML systems.
5. What Are Infinite Approvals And Why Are They Dangerous?
Infinite (unlimited) approvals allow a smart contract to spend an unlimited amount of a specific token from your wallet. If the contract has a vulnerability (like the arbitrary call flaw found in these protocols), a hacker can "command" the contract to send your tokens to their own address without your direct consent.
6. Can The Stolen Funds Be Recovered?
It is possible if the funds are moved to Centralized Exchanges (CEXs) or if the attacker agrees to a White Hat Bounty. AMLBot is currently monitoring all identified hacker addresses and will flag any movement to exchange compliance departments globally.