Hacked by a Dream Job: A Case Study on Web3 Job Scams

"Finally, I've got the job…No, you just got scammed :("
For many, receiving an offer is a moment of excitement. It's the recognition of skills, the chance for new prospects, and even the start of a dream career. But what happens when that dream turns into a misery?
Scammers are getting in with compelling schemes in the Web3 sphere, where speed matches innovation. Imagine being offered a role, only to discover it's a front for draining your crypto wallet. These aren't just random attacks — they're targeted, polished, and devastating.
In the recent case, AMLBot revealed how easily enthusiasm can be exploited and how critical it is to stay cautious.
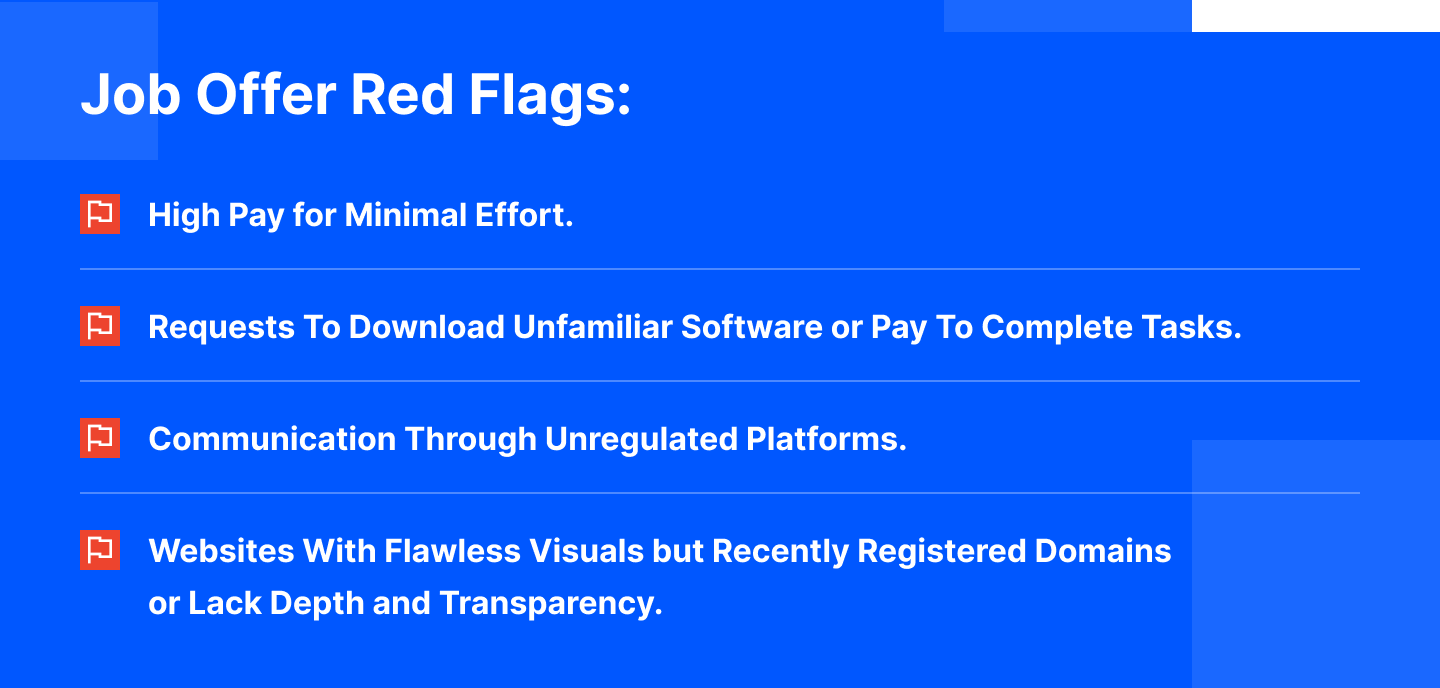
The Job Scam Core
According to data from the Identity Theft Resource Center, reports of job scams surged by 118% in 2023 compared to previous years. Scammers use various tactics to exploit their victims. Let's overview of the common threats and the warning signs:
- Job Ponzi Schemes and Task Scams. Enticing victims with high pay for simple tasks steps up into requests for upfront payments that ultimately lead to financial loss.
- Games and Beta Testing Scams. Malware disguised as blockchain games stealing sensitive data from compromised devices.
- Fake Recruiters and Social Engineering. Using persuasive tactics to trick individuals into sharing access or downloading harmful software.
- Freelance Platforms and Harmful Code. Targeting developers with seemingly legitimate projects, hiding malware in code repositories or scripts.
The Framework of a Scam
A victim had fallen prey to a job scam that used malware to drain his crypto wallets. The scam began when the job seeker was approached via Telegram by someone posing as a recruiter for a gaming project called “The Dinoverse”. He was offered an enticing Marketing Manager role. As part of the application process, he was asked to fill out a query and download a game installer to get to grips with the product. The installer contained malware designed to take down the device.
Later, the victim discovered that his crypto wallets had been targeted. Both the MetaMask and Exodus accounts were robbed of USDT and Ethereum. The attackers also tried to access staked funds but failed. By the time the theft was discovered, the scammers had deleted their Telegram account. Still, they were back under a slightly altered profile, luring more victims.
After the victim’s device was compromised, he contacted our team, enabling us to take action. AMLBot traced the stolen funds and proactively reported the perps' addresses to the relevant exchanges. We blocked 0.3 BTC and prevented the remaining funds from being laundered.
The hacker also accessed the victim's staked assets on the Keplr Wallet, such as INJ, ATOM, and others. Since unstaking these assets involves a 14-day waiting period before they can be sold, this delay turned out to be helpful for the victim. AMLBot's team created a script to instantly recover these funds once the waiting period ended, ensuring the hacker could not claim them. As a result, the victim recovered the funds, avoided further losses, and better understood how these scams operate. We are currently working on many similar cases. Expect more insights soon.

The Web3 field is risky. Stay informed, and remember — caution is your strongest asset!