Honey Trap: How Address Poisoning Scammed $50K — and How It Was Recovered

What Happened?
Earlier this year, a Czech company fell victim to an address poisoning scam scheme, resulting in the loss of $50,000+ in USDT. The scam exploited the company's operational routine, targeting its treasury wallet and leveraging address similarities to divert funds to a malicious actor's wallet.
The outgoing transaction was intended to be made from the company's treasury wallet to the company's wallet on Bitfinex. As the transaction history shows, almost all transactions from the treasury wallet were made to Bitfinex’s wallet, and the sender typically copied the wallet address directly from the transaction history.
Unfortunately, during this particular transaction, a malicious wallet address that closely resembled the legitimate company wallet was mistakenly copied. A perpetrator had used this address to poison the company’s wallet by sending a small incoming transfer beforehand, thus embedding their address in the transaction history.
The company contacted AMLBot regarding the theft 1 day after the incident to assist with the investigation. They did not contact the police immediately because they did not know about the legal procedure in that situation.
AMLBot quickly identified the fraudulent transaction and traced the stolen funds. Also, the team flagged the malicious wallet and worked with relevant parties to freeze the funds and gather all necessary documentation to support the case, ensuring they could not be moved further.
After one month, the company filed a police report, as the blockchain forensic firm’s experts suggested, as a necessary step to initiate a potential recovery. Throughout the process, AMLBot closely collaborated with the Czech police, providing a detailed investigation report and supporting documentation to assist in the case. Reflecting on the experience, the affected company shared their thoughts:
"I would like to express my gratitude for the professional assistance in resolving our issue. Thanks to the effective work of the team, we were able to recover funds that were stolen by fraudsters. The AMLBot team demonstrated a high level of expertise and efficiency throughout the process."
"I would especially like to highlight their support and attention to detail — they helped us not only with the recovery process but also with legal matters, which significantly simplified the situation. Despite the complexity of the case, everything went smoothly and quickly."
"I highly recommend AMLBot to anyone facing similar issues. We will definitely turn to them in the future if any new challenges arise. Thank you for the excellent work!"
Detailed Scheme of Address Poisoning Attack
The attackers start by creating wallet addresses that closely resemble legitimate ones, matching key details like the first or last few characters.
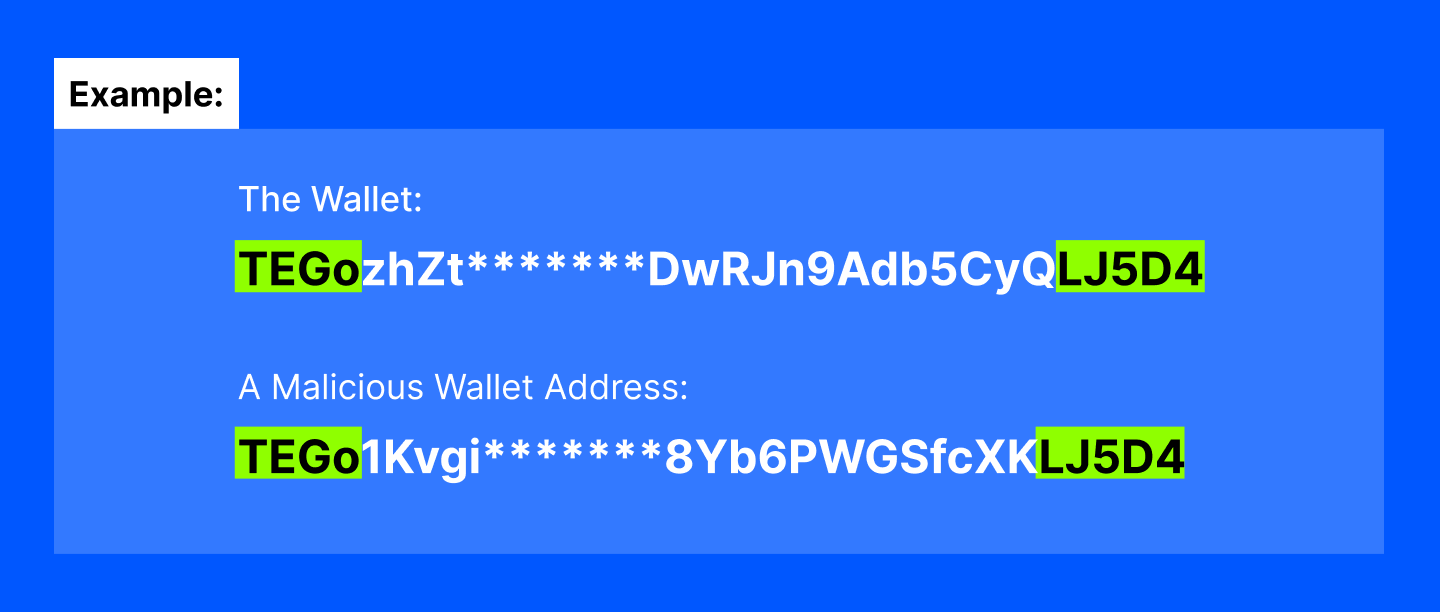
These fake wallets, called "honey pot addresses," are crafted to appear credible in transaction histories. To make these addresses functional, attackers use a primary storage address to allocate the necessary energy and bandwidth on blockchains like Tron, allowing the fake wallets to process transactions without additional costs.
The attackers then send small amounts of USDT (usually less than $1) to the victim's wallet from the honey pot address. These small transfers ensure the malicious address appears in the victim’s transaction history, creating the illusion of a legitimate prior transaction. When the victim needs to make a transfer, they may quickly copy this fake address from their history without verifying it.
Once the funds are mistakenly sent, the attackers quickly move to launder the stolen assets. They often use platforms to exchange the funds between USDT and TRX, obscuring the transaction trail. The laundered funds are then processed through crypto exchanges or other swapping services, making them even more challenging to trace.
The attackers may reinvest part of the stolen funds to keep their operation running. This includes funding new honey pot addresses or maintaining the energy and bandwidth needed for more transactions. By repeating this process, they can continuously target new victims and scale their attacks.
What makes address poisoning so effective is its subtlety. The scam blends seamlessly into regular wallet activity, preying on users' habits of relying on transaction histories without careful verification.
How to Protect Yourself from Address Poisoning Attacks?
Address poisoning scams work because they exploit habits — our tendency to copy and paste from transaction history without double-checking. The good news? A few simple precautions can keep your crypto safe from these deceptive tactics.

1️⃣ Always Verify, Never Assume
Before sending crypto, take an extra moment to verify the entire wallet address, not just the first and last few characters. Scammers rely on visual similarities, so manual verification is your first line of defense.
2️⃣ Save Trusted Addresses Manually
Instead of copying from transaction history, create an address book in your wallet or save frequently used addresses separately. This eliminates the risk of mistakenly selecting a poisoned address.
3️⃣ Be Wary of Small, Random Incoming Transactions
If you notice unexpected micro-transactions—especially from unknown addresses — this could be a red flag that your wallet is being primed for an address-poisoning attack.
4️⃣ Use Wallets with Address Whitelisting
Some crypto wallets allow whitelisting, meaning you can pre-approve addresses for transactions. If your wallet supports this feature, enabling it adds another layer of security against copy-paste mistakes.
5️⃣ Perform an AML Check Before Sending Large Transactions
Before transferring significant funds, run an AML check on the recipient’s address. A quick scan can reveal whether the wallet has suspicious ties, helping you avoid falling into a scam trap.
6️⃣ Educate Your Team & Implement Internal Controls
For businesses handling crypto transactions, awareness and strict security procedures are crucial. Implement multi-step verification processes and train staff to recognize scam tactics.
While address poisoning attacks are sneaky, they aren't unstoppable. By staying vigilant, using secure practices, and leveraging AML tools, you can ensure your funds remain exactly where they belong — safe and under your control.
Need Help Investigating a Suspicious Transaction?
If you’ve fallen victim to an address poisoning attack or suspect fraudulent activity, don’t wait — our blockchain investigation experts can help. AMLBot specializes in tracing stolen funds, identifying fraudulent wallets, and assisting with fund recovery.