🚨 Joint Intel Strike — DeepCode × AMLBot Trace “1688shuju,” a Darknet Seller of Verified Exchange Numbers

On 22 August 2025, the DeepCode intelligence team identified a darknet marketplace listing by the actor “1688shuju” on darkforums[.]st offering large batches of verified phone numbers tied to major cryptocurrency exchanges (Binance, OKX, Coinbase, KuCoin, HTX). During an undercover engagement, DeepCode obtained a payment endpoint used to purchase the datasets. AMLBot performed on-chain tracing of wallets that funded this endpoint, clustered likely buyer wallets, and flagged one wallet with prior illicit reports. This joint operation exposes a systematic, high-volume credentials market that elevates the risk of account takeover (ATO), SIM-swap fraud, and targeted social-engineering at scale.
🚨 According to https://t.co/hj3mMNUJXf, on August 22, 2025, threat actor “1688shuju” was found offering verified phone numbers linked to major exchanges: @binance, @kucoincom, @coinbase, @okx, @HTX_Global - on a darkforums[.]st pic.twitter.com/mJUd80zm16
— AMLBot (@AMLBotHQ) October 3, 2025
Why This Matters (Quick Takeaways)
(а) Scale: Listings claim hundreds of thousands to over a million phone numbers already linked to verified exchange accounts, enough for mass ATO and automated fraud campaigns. (Table Below)
(b) High-Value Infrastructure: Verified phone numbers (numbers already used for 2FA, account recovery, or SMS-based confirmations) substantially lower the cost and increase the success rate of account takeover attempts.
(c)Cross-Team Impact: DeepCode’s operation found an active payment endpoint. AMLBot’s blockchain tracing mapped funds flowing to that endpoint and flagged buyer wallets with prior illicit reports. That combination turns an OSINT lead into actionable data for exchanges and law enforcement.
Context from Recent Reporting
Independent threat-intel teams have been documenting a broader, accelerating trend of crypto-exchange user data, including phone numbers, being offered on dark-web forums and closed channels.
In June 2025, ZeroFox observed actor “Machine1337” advertising “freshly scraped and verified” mobile number lists on the XSS forum, underscoring demand for phone-based targeting. In March 2025, Cointelegraph (citing Dark Web Informer) reported a listing for ~100,000 Gemini user records that included names, emails, and phone numbers. Gemini noted that much of it appeared to be a re-aggregation of older data, indicating that some “new” dumps are repackaged. SOCRadar likewise highlighted alleged OKX-related data listings in mid-2025, reflecting continued interest in exchange-linked datasets. At the same time, exchanges such as Binance have publicly denied several viral “mega-leak” claims (e.g., the 12.8M-user rumor in Sept 2024), warning that hype and hoaxes frequently contaminate the ecosystem. However, even when some dumps are exaggerated, verified exchange-tied phone numbers function as “Trojan Horses” for SIM-swaps, smishing, and targeted social engineering – a pattern recently flagged by industry reports.
The Advertised Inventory — What “1688shuju” Listed
(Quoted figures are from the joint intel announcement and the forum listing highlighted by DeepCode/AMLBot)
These numbers indicate a commercialized operation, not the opportunistic leakage — the scale suggests systematic collection, validation, and packaging of exchange-linked phone records for resale.
How The Joint Investigation Unfolded (Step-By-Step)
OSINT / Undercover Discovery (DeepCode)
DeepCode analysts discovered a DarkForums thread and related marketplace postings where the actor 1688shuju advertised a phone-number “checker” and batches of verified numbers. During an undercover purchase, DeepCode recovered the actor’s payment endpoint –
bc1qt9f82xyvvdql3ypma43vccutv60kjsdzee0ltpw7p4742augxgjs24x77m – which was subsequently identified as an OKX deposit address.
Blockchain Tracing & Attribution (AMLBot)
AMLBot ingested the payment endpoint and traced all inbound transactions, clustering likely buyer wallets. Cross-checks against our risk intel flagged at least one funding wallet with prior illicit reports (public shorthand: bc1qpf...ms4v).
Note: We provided wallet clusters, hashes, and timestamps to OKX compliance with a recommendation for immediate review (phone-change/recovery events, new device logins, and correlated withdrawals).
Blockchain Evidence: Visualizing the Payment Trail
To substantiate the on-chain findings, AMLBot analysts produced a transaction-flow visualization via Tracer for the 1688shuju endpoint.
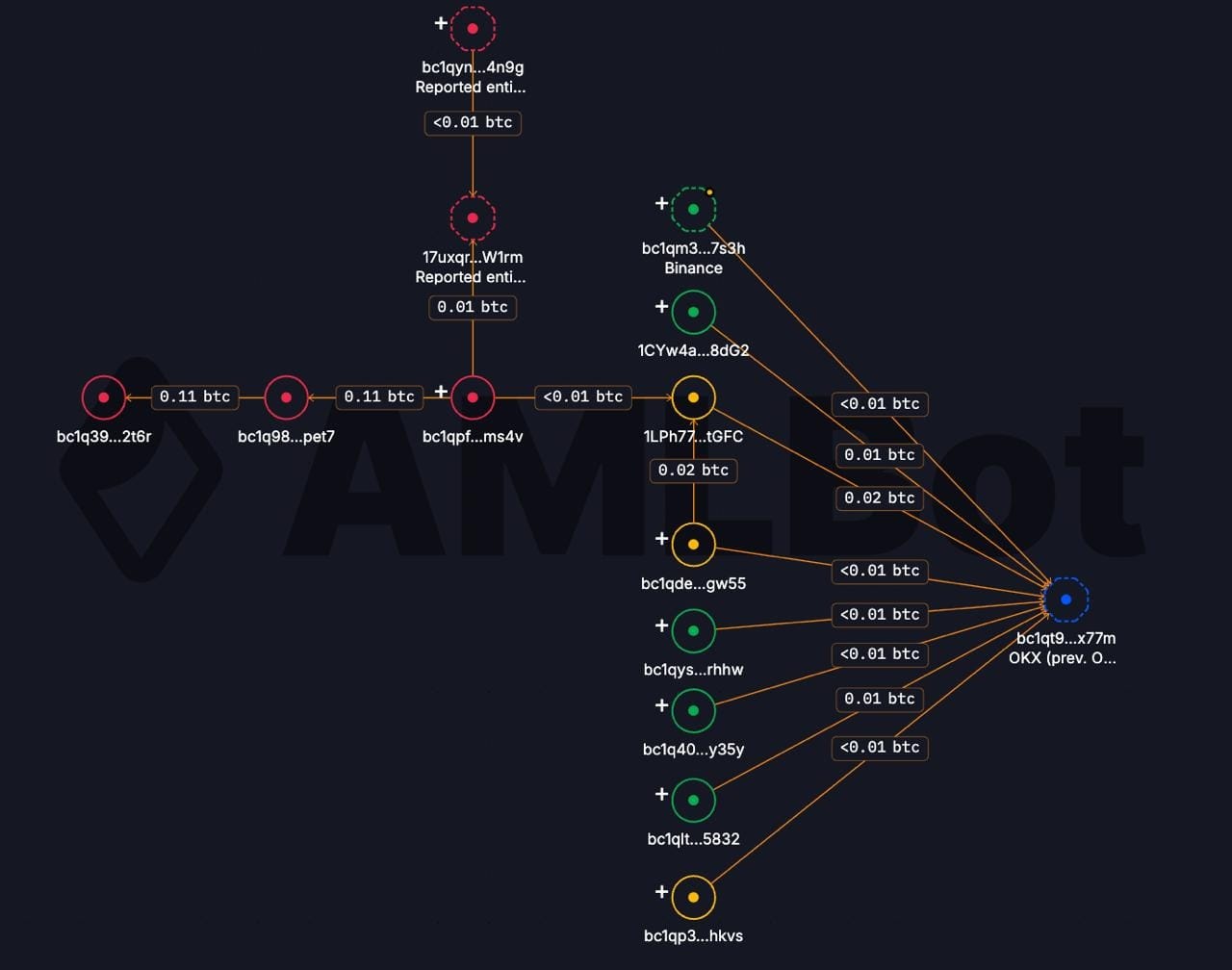
The Figure 1 illustrates how multiple small BTC transactions originating from several buyer wallets converge into a single OKX deposit address – the final node in blue. On the left side, red nodes represent wallets that have already been reported in prior AML investigations and are linked to other illicit activities on darknets. The middle layer (yellow and green nodes) shows intermediary hops and newly identified buyer wallets that performed micropayments (mostly <0.01 BTC). All these flows eventually merge at the OKX address, confirming that the marketplace’s revenue from verified-number sales was being routed through a regulated exchange.
In simple terms: What looks like ordinary small deposits in an exchange account actually corresponds to dozens of micropayments from darknet buyers — a laundering pattern that AMLBot’s clustering algorithm detects and ties back to a single threat actor.
Downstream Risks — How These Numbers Can Be Abused
- Large-Scale Account Takeover (ATO): Verified phone numbers tied to accounts on centralized exchanges can be used to intercept SMS-based 2FA or to social-engineer carrier support for SIM swaps. Hundreds of thousands of validated numbers erode the effort/cost needed to mount high-success ATO campaigns.
- Credential Stuffing + Takeover Pipelines: Paired with leaked emails or reused passwords, these phone numbers convert low-cost credential lists into takeover-grade toolkits.
- Targeted Phishing / Vishing Campaigns: Verified numbers enable tailored voice-phishing (Vishing) or SMS scams that impersonate exchanges, raising the likelihood of mass victimization.
- Market For Automated Abuse: The quantities advertised support automated tools to attempt bulk account recovery, bypassing rate limits and anti-fraud controls unless exchanges act quickly.
What Users Should (And Can) Do. Practical Recommendations
Even though these rules may sound like Privacy 101, we want to emphasize them again — because the latest darknet cases show that one weak link (like an exposed phone number) can still open the door to full account compromise. So, before it happens to you, make sure you’re covered:
- Keep the majority of your assets in hardware wallets or multisignature (multisig) setups, not on exchanges. Centralized exchanges are convenient but also prime targets for social-engineering and phishing campaigns that begin with leaked phone numbers.
- Replace SMS-only 2FA with authenticator apps or hardware keys. SMS messages are the easiest point of failure in account security. Use Google Authenticator, Authy, or a YubiKey instead. These generate one-time codes locally, eliminating risks of SIM-swap, SMS interception, or number cloning. If your exchange still allows SMS 2FA, deactivate it after switching to app-based or hardware authentication.
- In your account settings, regularly review the linked phone numbers, emails, and recovery devices. If you spot an update you didn’t authorize – act fast: lock withdrawals and contact support. Set alerts (where supported) for account changes or new device logins.
- Scammers use leaked numbers to impersonate support agents. No legitimate exchange will EVER ask for your password, seed phrase, or full 2FA code via phone, Telegram, or email. Hang up, verify the domain, and contact the exchange through official support channels only. In addition, report suspicious outreach. Most exchanges have a security@ contact or an in-app report option.
This report is part of our ongoing joint intelligence series with DeepCode, focused on identifying and tracing emerging darknet threats targeting the crypto ecosystem. If you want to explore other investigations from this collaboration – follow our updates on X (Twitter) for the latest releases.
FAQ
What Did AMLBot And DeepCode Uncover About The Darknet Actor “1688shuju”?
DeepCode first identified “1688shuju” on darkforums[.]st advertising verified phone numbers linked to major exchanges, including Binance, OKX, Coinbase, KuCoin, and HTX. AMLBot later traced the payments tied to those listings and confirmed that buyer transactions converged into an OKX deposit address — proving that the illicit trade was monetized through a regulated exchange.
Why Is The Sale Of Verified Exchange-Linked Phone Numbers By “1688shuju” Considered A High-Risk Incident?
Verified phone numbers are already used for 2FA, password resets, and account recovery. Having access to such data allows attackers to perform SIM Swaps, intercept authentication codes, or trigger recovery workflows on legitimate exchange accounts, enabling direct account takeover (ATO).
What Did AMLBot’s Blockchain Tracing Reveal About The “1688shuju” Payment Endpoint?
AMLBot traced the specific payment endpoint bc1qt9f82xyvvdql3ypma43vccutv60kjsdzee0ltpw7p4742augxgjs24x77m, identified as an OKX deposit address. The analysis showed dozens of micropayments (mostly <0.01 BTC) from buyer wallets, several of which were previously reported for illicit activity, merging into that OKX address.
How Did DeepCode and AMLBot Confirm That The OKX Deposit Address Was Connected To The “1688shuju” Operation?
During an undercover purchase, DeepCode obtained the payment address directly from the actor. AMLBot validated it on-chain, observing a repeating flow pattern typical of darknet marketplace transactions — small, structured payments from multiple independent sources converging into a single centralized wallet, confirming its operational role in the marketplace.
