Tracing WazirX Hack with AMLBot Pro

The $235 million hack on Indian cryptocurrency exchange WazirX on July 18 has intensified scrutiny over the security of digital asset platforms and sparked a comprehensive investigation.
The hacker moved approximately $234.9 million worth of funds to a new address, using assets funded through the cryptocurrency mixer Tornado Cash. The stolen funds were diverse, including Tether (USDT), Pepe (PEPE), and Gala (GALA), which were quickly converted into Ether (ETH) to obscure the trail. The wallet also contained $100 million in Shiba Inu (SHIB), $52 million in ETH, $11 million in Polygon (MATIC), and smaller amounts of other tokens.
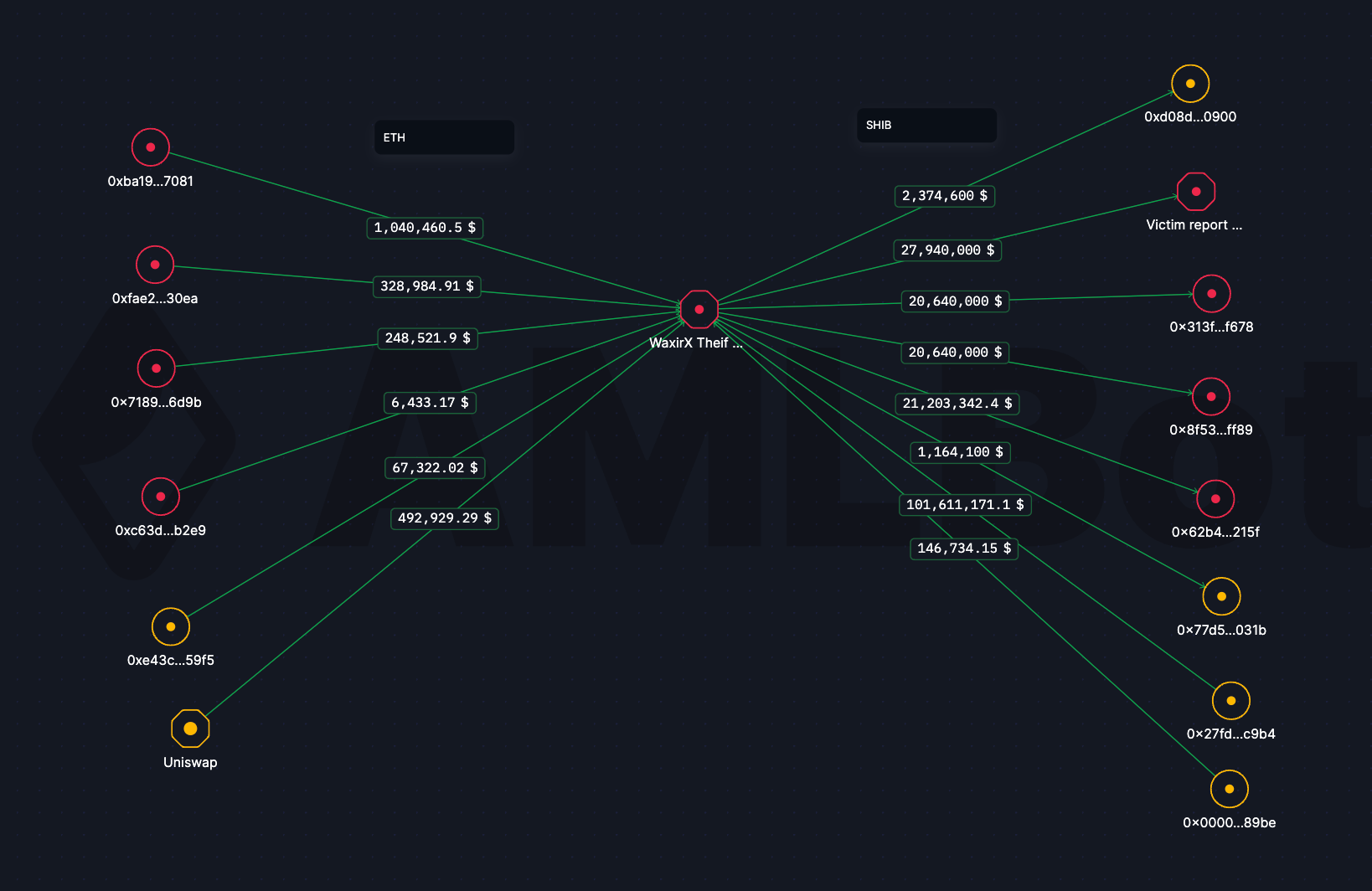
Investigation Details and Security Analysis
Meir Dolev, co-founder and CTO of Cyvers, provided insights into the attack’s mechanics. Although the exact vulnerability remains unknown, several key details emerged:
- Multisig Wallet System: WazirX employs a multisig wallet requiring four signatures for transactions, with Liminal providing the final signature. The wallet has a whitelist policy, limiting transactions to specific addresses.
- Attack Vector: The hacker used two addresses—one to initiate transactions and another to receive funds. The initiating address was funded via Tornado Cash.
- Malicious Contract: Eight days before the hack, the attacker deployed a malicious contract to alter the implementation of the WazirX wallet. Just before the exploit, the attacker used the signatures of WazirX and Liminal to change the wallet’s implementation to the malicious contract, enabling unauthorized transactions.
Dolev speculated that the attacker likely compromised WazirX endpoints or laptops, possibly employing a user interface (UI) hijack on Liminal’s side to make the fraudulent transaction appear legitimate. Liminal Custody confirmed its platform's security, attributing the breach to a self-custody multisig smart contract wallet created outside its ecosystem.
Explore the visualization in detail:
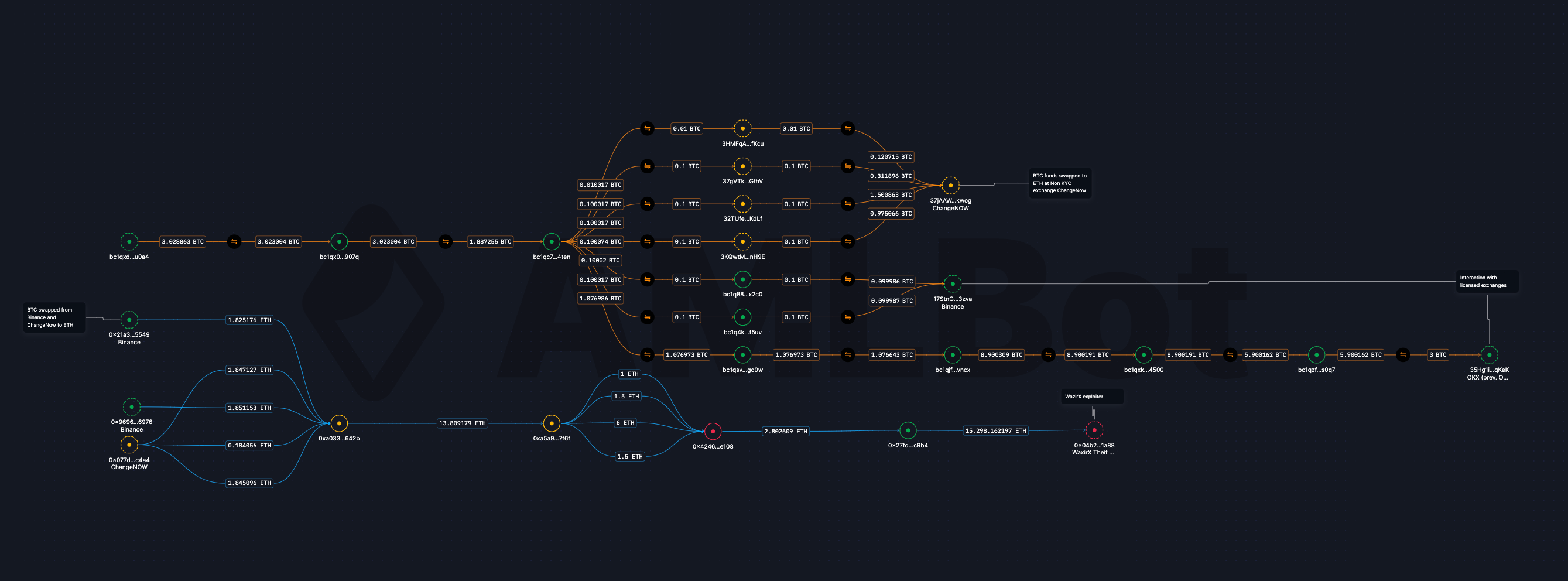
North Korean Involvement Suspected
Investigators have not ruled out North Korean involvement, pointing to patterns characteristic of North Korean hackers. The Lazarus Group, a notorious North Korean criminal organization, is suspected due to its history of significant cyber exploits, including the $600 million Ronin Bridge incident.
Market Impact and Recovery Efforts
The hack caused notable market turbulence, especially affecting SHIB, which dropped 10% in value. Attackers began converting SHIB to ETH almost immediately, exchanging billions of SHIB tokens for millions in ETH.
WazirX has taken significant steps to recover the stolen funds, including:
- Collaboration with Exchanges: WazirX is working with over 500 exchanges to block the identified addresses. Many exchanges are cooperating with WazirX to aid recovery efforts.
- Legal Actions: In addition to filing a police complaint, WazirX is pursuing further legal actions to hold the perpetrators accountable.
- Ongoing Investigations: The exchange is actively working with authorities, including the Financial Intelligence Unit and the Indian Computer Emergency Response Team, to investigate the breach and prevent future incidents.
Conclusion
The WazirX hack underscores the critical importance of security in the cryptocurrency sector. As the investigation continues, it will likely prompt increased scrutiny and possibly lead to enhanced regulatory measures aimed at protecting investors and ensuring the integrity of digital asset platforms in India.
About AMLBot: Our blockchain investigation services have successfully recovered millions in stolen assets, working closely with law enforcement across the Globe. AMLBot Pro, our advanced blockchain analytics tool, is tailored for law enforcement and compliance teams, ensuring swift and effective asset recovery and compliance. Choose AMLBot for cutting-edge technology and proven results in crypto compliance.
Blockchain Investigation Experts: Contact Us for Lost Crypto Recovery