Trust Wallet Browser Extension Compromise: $7.3M Lost in a Supply-Chain Attack

TL;DR: A second wave of the SHA1-Hulud worm compromised Trust Wallet’s browser extension, leading to the theft of mnemonic phrases and over $7.3 million in crypto losses. The attackers exploited infected NPM Packages, deployed a malicious extension update, and laundered funds through cross-chain bridges, swap services, and centralized exchanges.
This article breaks down how the attack worked, where the funds went, and what the on-chain patterns show.
What Happened?
In November 2025, blockchain security researchers identified a second iteration of the SHA1-Hulud Worm — a supply-chain attack targeting NPM Packages. After execution, the malware scanned the NPM Packages the victim had access to and injected malicious code that allowed it to self-replicate. As the infection spread, more than 700 packages were compromised, impacting thousands of developers. During this process, the attackers gained access to sensitive credentials, including Trust Wallet’s browser extension source code and the Chrome Web Store API Key. With that key in hand, they were able to upload a malicious version of the Trust Wallet Browser Extension, released as version 2.68.
@TrustWallet users lost over $7.3 million in a second layer of SHA1-Hulud worm attack. “He who controls the spice controls the universe” – Trust Wallet hackers’ server responded to an HTTP query. So did the threat actor indeed had plans within plans within plans as in Herbert’s… pic.twitter.com/xuKp018poB
— AMLBot (@AMLBotHQ) January 9, 2026
How the Wallets Were Drained
According to SlowMist’s analysis, the malicious extension operated quietly in the background. Once installed, it iterated through all wallets stored inside the browser extension, extracted mnemonic seed phrases in plaintext, and transmitted them to an attacker-controlled server at api.metrics-trustwallet[.]com.
At that point, no additional exploit was needed. With full access to the seed phrases, the attackers could reconstruct wallets at will and drain funds directly. It was a full private key compromise — the most severe category of wallet security breach.

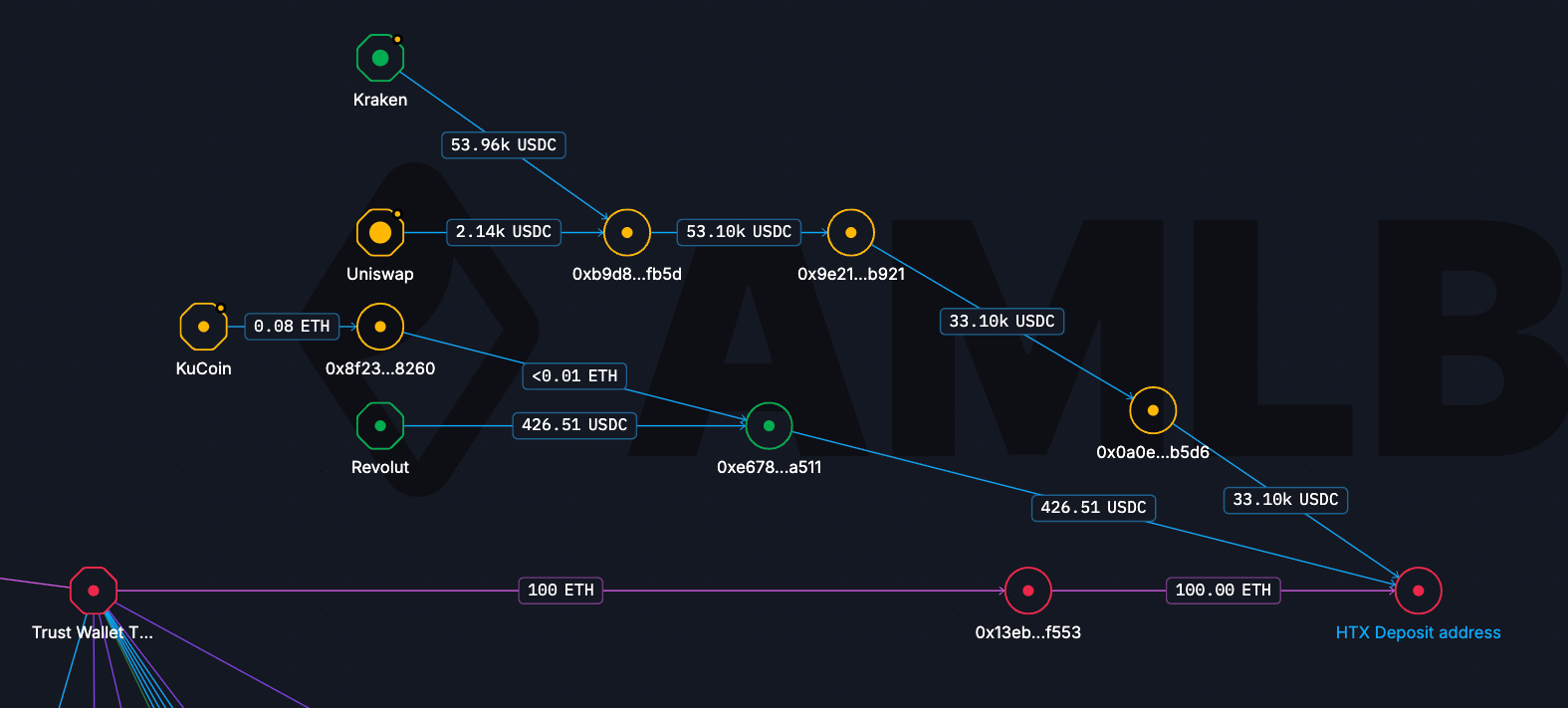
Following the Money: Ethereum Flows
On Ethereum, the attackers operated through at least ten primary addresses. From those addresses, funds were moved in a deliberately fragmented way. A total of 76 ETH was sent to FixedFloat in multiple uneven batches, while a separate transfer of 25 ETH was routed to another address where the funds remain dormant.
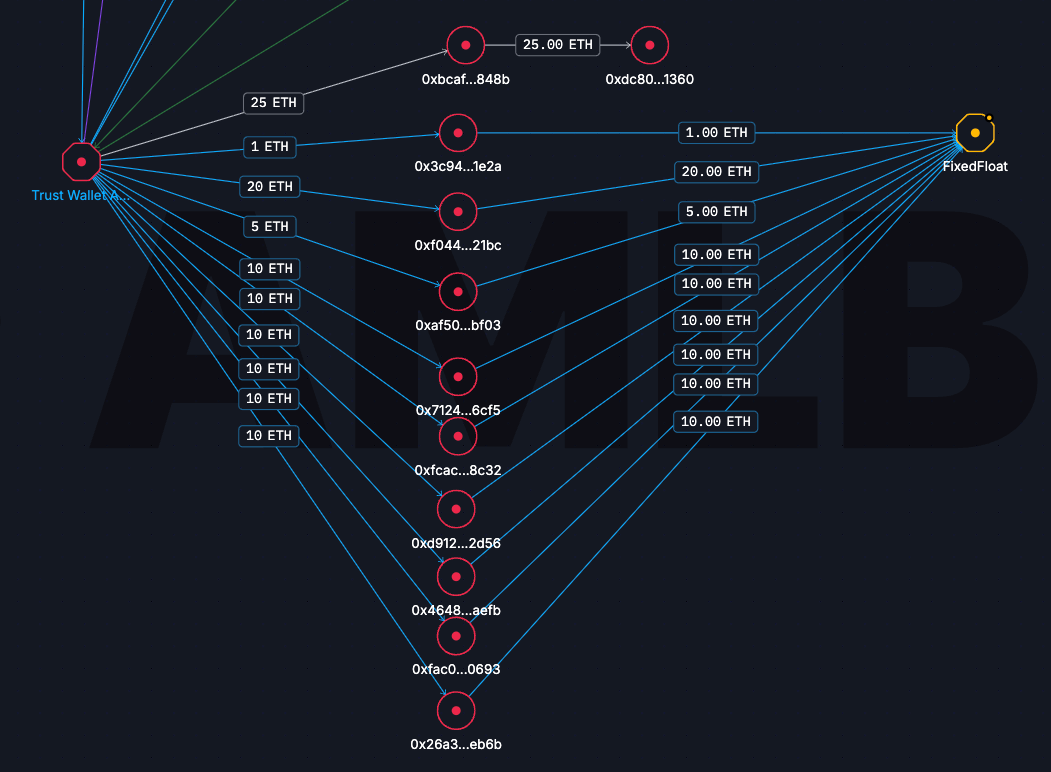
In parallel, large stablecoin and ETH flows were directed to ChangeNOW. Specifically, 442,470 USDT and 279.3 ETH were transferred to the service, consistent with patterns observed in other recent laundering operations. Rather than consolidating funds, the attackers split and staggered transactions, preparing them for cross-chain movement.
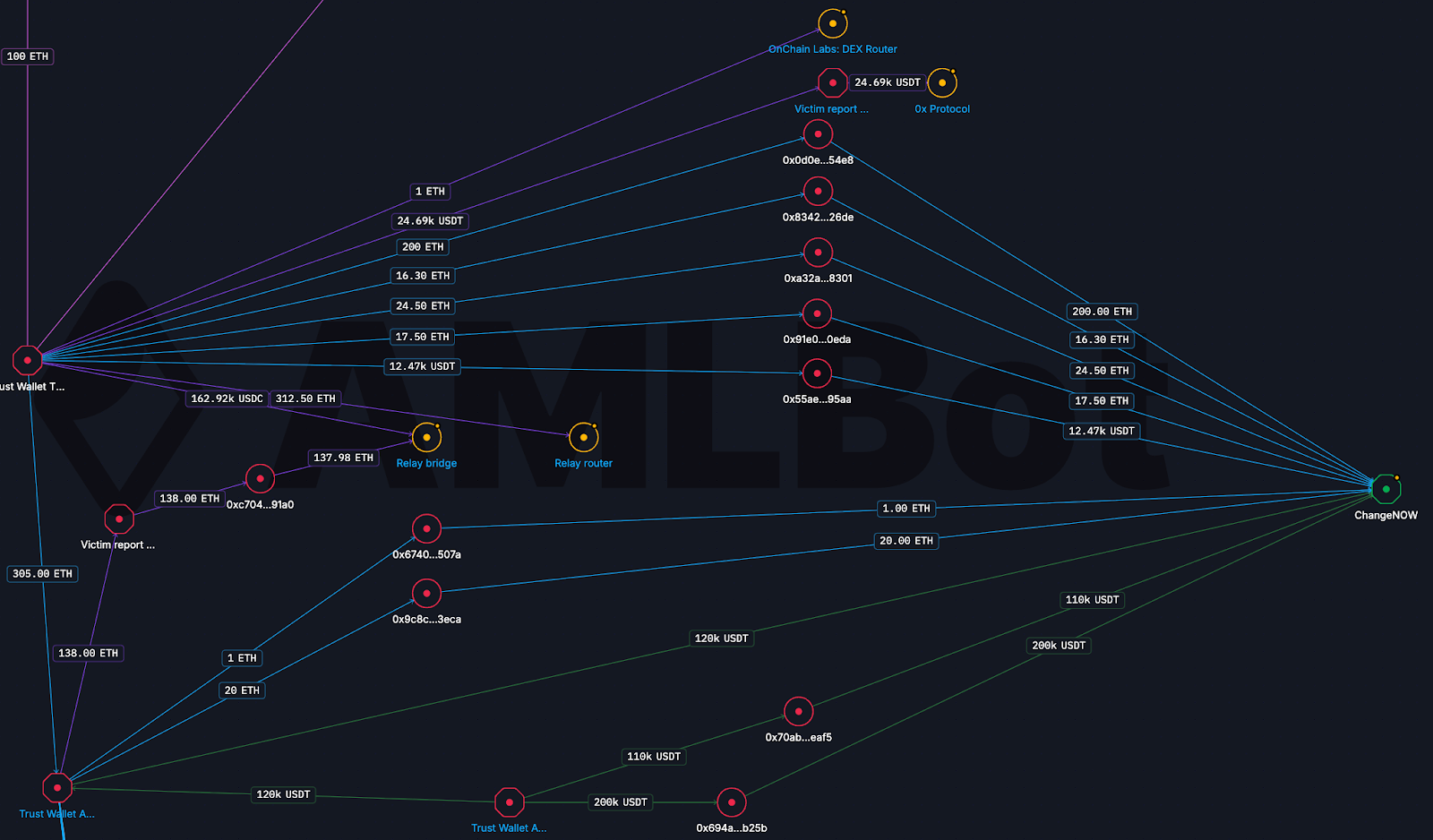
Cross-Chain Laundering via Bridges
As in many modern crypto hacks, cross-chain bridges played a central role in obfuscation. Significant amounts of ETH, USDC, and USDT were bridged out of Ethereum, primarily through Relay.link, with additional routing through 0x Protocol and the Onchain Labs DEX Router, which is affiliated with OKX.
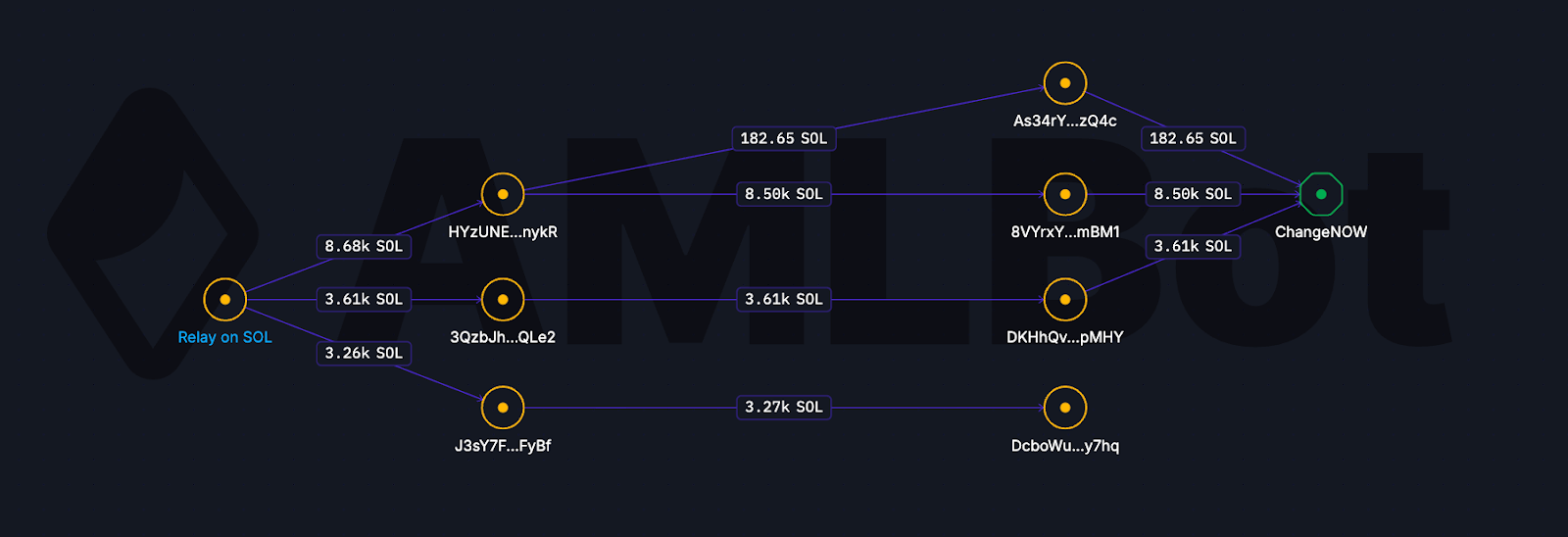
After crossing chains, the assets were swapped into Solana. In total, the attackers accumulated 15,550 SOL, which was then distributed across three Solana addresses. From there, 12,280 SOL was moved through several intermediary wallets, while 3,270 SOL remains inactive on a separate address, suggesting either operational delays or intentional long-term storage.
Centralized Exchanges Were Used — Repeatedly
One of the most revealing aspects of this case is the attackers’ direct use of centralized exchanges. On Ethereum alone, 200 ETH was deposited almost immediately into exchange-controlled addresses, with 100 ETH sent to KuCoin and another 100 ETH to HTX.
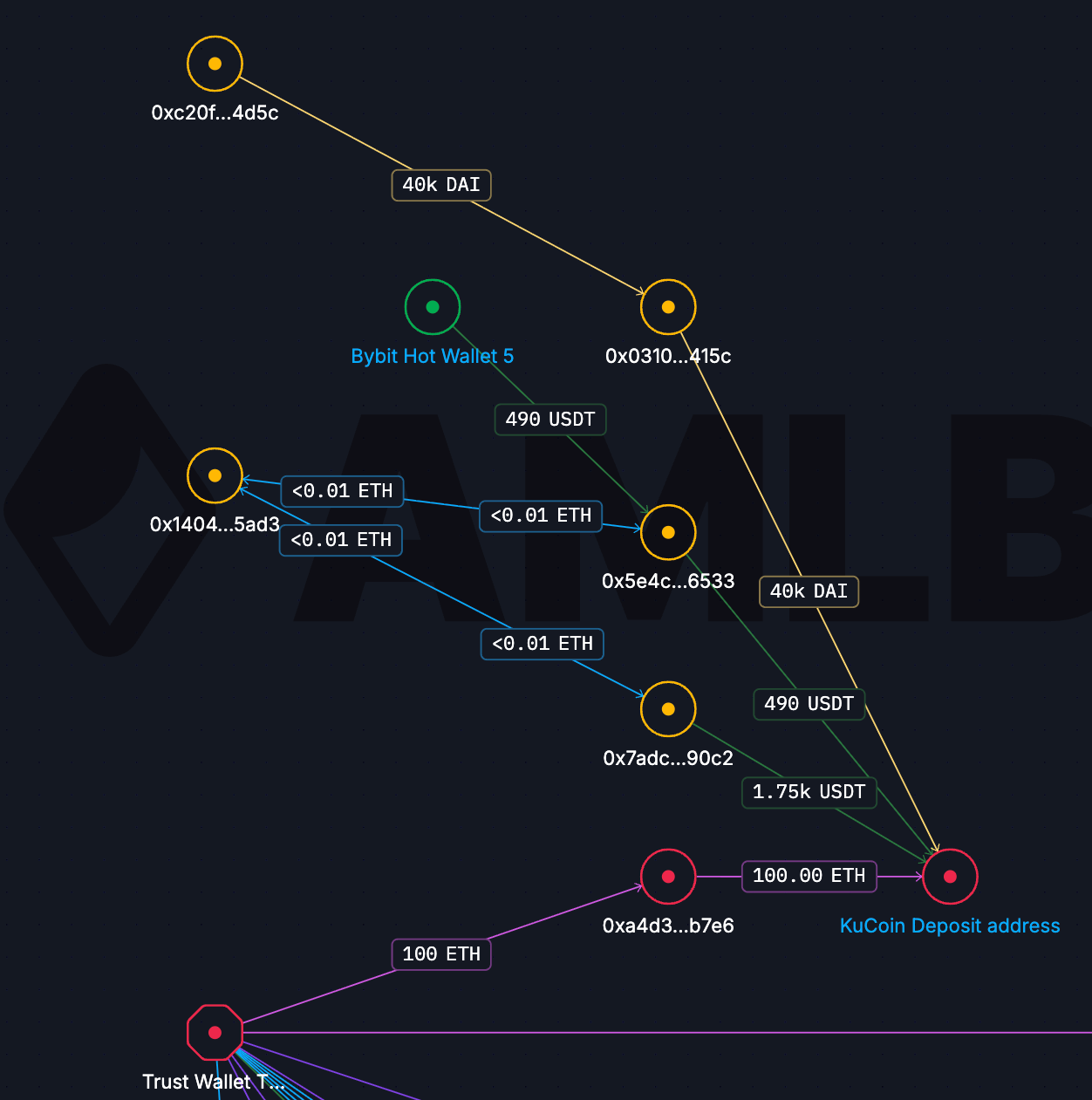
A closer look at the KuCoin deposit address showed that it had been active weeks before the hack and continued receiving funds weeks afterward. This suggests that the attacker reused an existing, operational account rather than creating a one-off deposit address for laundering. The HTX address, by contrast, was not reused after the incident, although it had received USDT deposits prior to the attack, indicating that it may have been pre-positioned.
Bitcoin Tracing Shows the Same Playbook
Tracing the Bitcoin flows revealed a nearly identical laundering strategy. Most BTC was routed through instant swap services such as ChangeNOW and FixedFloat, mirroring the Ethereum behavior. Some BTC was transferred cross-chain to Solana and remains parked on receiving addresses, while another portion was deliberately left dormant on native Bitcoin wallets. In addition, 7.5 BTC was sent directly to a KuCoin deposit address.
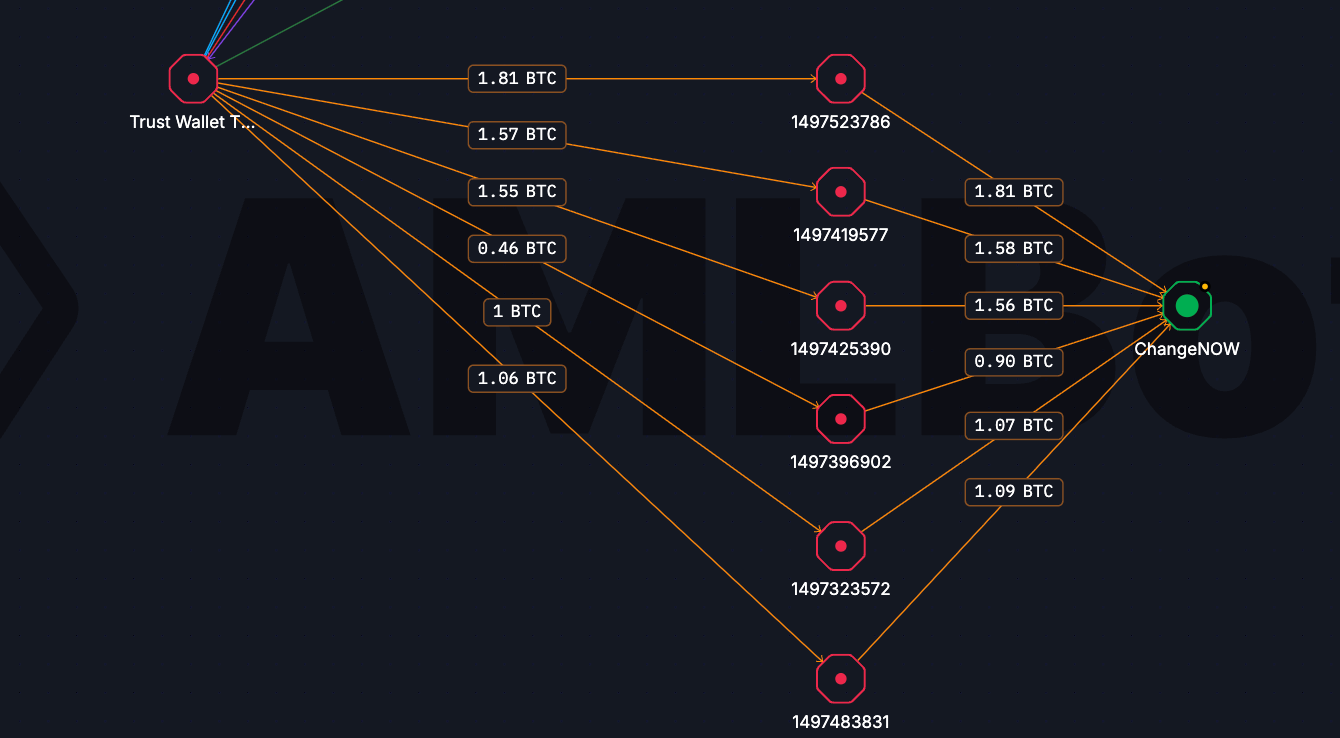
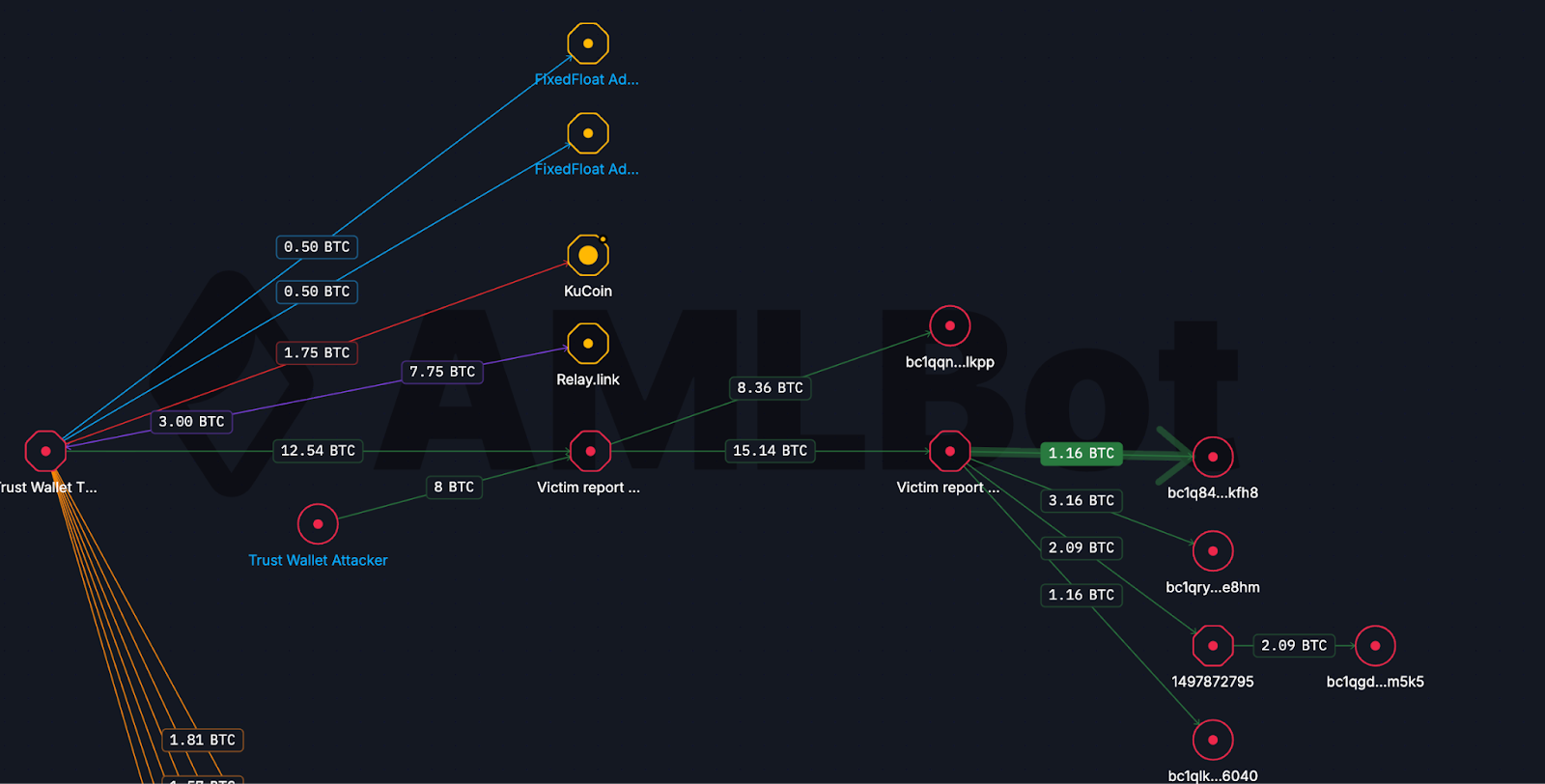
The repetition across chains makes the intent clear: the attackers relied on a consistent, well-tested laundering stack rather than improvising per asset.
This incident goes beyond Trust Wallet as a single product failure. It highlights how supply-chain attacks remain one of the most underestimated risks in crypto, especially when browser extensions are involved. Once a seed phrase is exposed, all downstream security assumptions collapse, regardless of how robust the underlying blockchain infrastructure may be.
The case also demonstrates how modern attackers blend decentralized tools with centralized infrastructure. Cross-chain bridges, instant exchangers, and centralized exchanges are not used in isolation but as complementary components of a single laundering workflow.
Why Early Detection Matters
Once funds are fragmented, bridged, swapped, and distributed across multiple chains, recovery becomes exponentially more difficult. Every additional hop reduces visibility and increases response time.
This is why early detection is critical. Tools like AMLBot Tracer are designed to surface abnormal transaction behavior before assets become irreversibly dispersed. By identifying suspicious flows, interactions with instant exchangers, and exposure to centralized exchange deposit addresses at an early stage, investigators gain a narrow but crucial window for action.
Modern crypto crime almost always leaves traces on-chain. The difference between attribution and disappearance often comes down to how quickly those traces are identified and acted upon.
-AMLBot Team
Connect with AMLBot:
🔗 Website
🔗 Telegram AML Bot
🔗 AMLBot Support Team
🔗 AMLBot LinkedIn







