Understanding the Basics of Cryptocurrency Security: Private Keys, Public Keys, and Seed Phrases

Cryptocurrency is witnessing a massive increase in its usage owing to the novel benefits it brings like decentralization and more. Nevertheless, those wanting to use cryptocurrency may wonder how they remain secure despite utilizing decentralized networks like blockchains. While several aspects are at play, an important part of blockchain and cryptocurrency security is public key cryptography (PKC).
Essentially, data in the form of cryptocurrency and its transactions can get encrypted and decrypted safely using cryptographic keys known as public and private keys, respectively. This allows users to store the cryptocurrency transferred to them securely and solely initiate transactions with the stored cryptocurrency. The keys act like banking accounts and passwords while initiating transactions over the blockchain.
The keys alongside seed phrases are integral parts of crypto wallets.
Seed phrases are analogous to banking platforms' password recovery measures. However, they add an extra layer of protection to the cryptocurrency present in wallets when their private keys are not accessible.
A wallet's keys and seed phrases are needed to receive, store, and transfer cryptocurrency safely. Because only a little can be done when cryptocurrency gets stolen or lost, it is important to understand how each of the three wallet components must be handled and used.
Private Keys
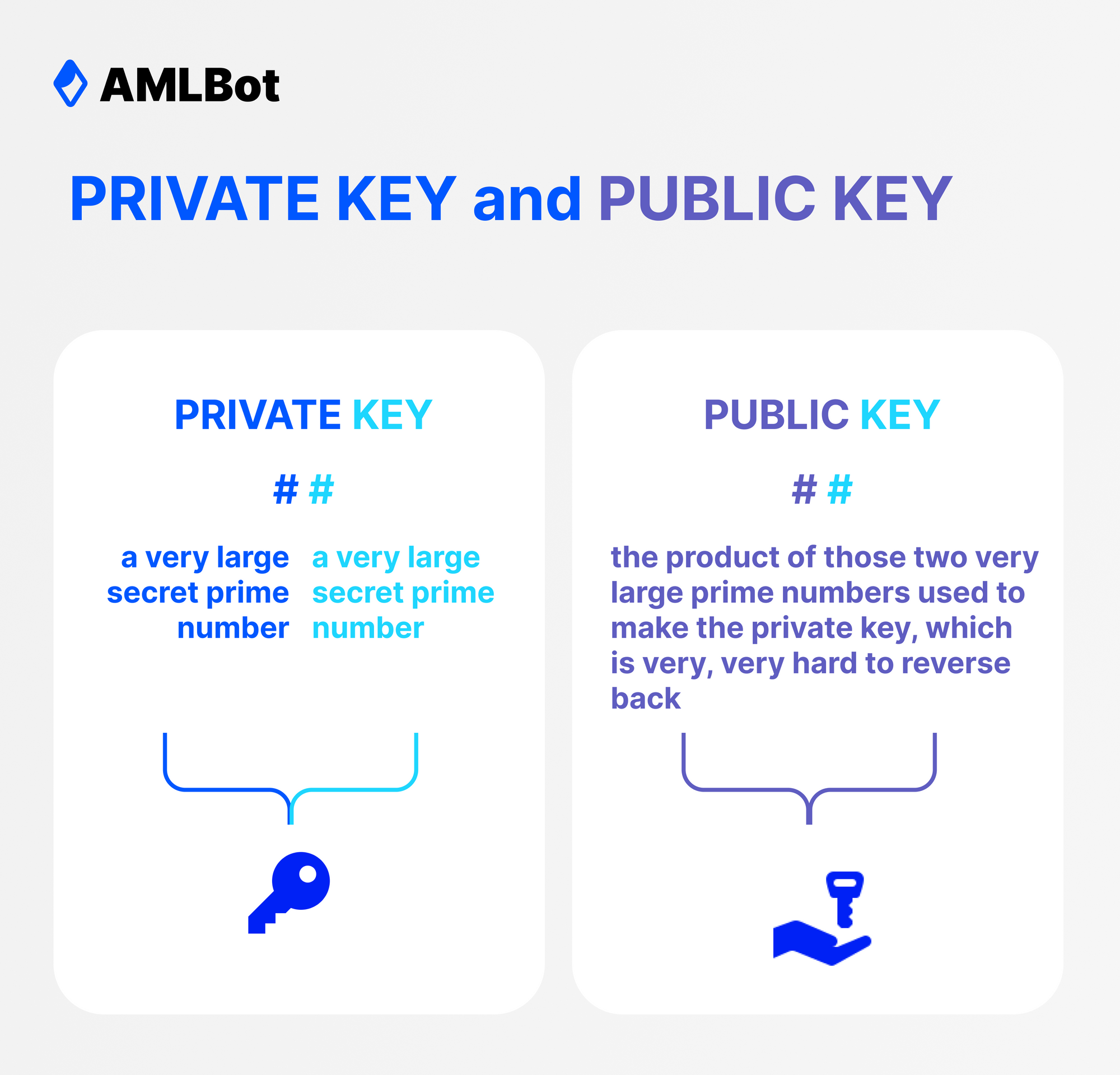
Private keys are a long set of alphanumeric characters responsible for decrypting the cryptocurrency associated with user wallets and, thus, allowing them to access it for transaction purposes. So, private keys act as passwords to their specific wallets, allowing users to dig into what they hold.
For that reason, private keys must be stored safely away from other people. Anybody accessing a wallet’s private key can access the funds in that wallet. 2022 marked around $3.8 billion in stolen cryptocurrency, out of which a large portion was linked to bad actors accessing user and enterprise wallet private keys. Therefore, self-storage of private keys in secure locations is always suggested. A best practice is to store them away from networks, keeping hacking attempts to grab the keys away.
Air-gapped devices, dedicated hardware cold wallets, and noting keys on paper – paper wallets – are some safer methods. When turning to electronic storage devices, it is best practice to enable two-factor authentication (2FA) or pin protection to add a layer of security. It is also advisable to leave these devices and paper wallets, whatever is being used, within safes and deposit boxes.
However, there are instances where private keys become inaccessible due to issues like theft, users losing their storage devices, or the material of paper wallets deteriorating. Losing private keys can mean the funds stored in their respective wallets can get trapped forever – unless the wallet came with a seed phrase (more on seed phrases later) used to regenerate its private keys from the master private key.
All private keys generated by a wallet stem from a master private key, acting as the root of all key pairs existing in that wallet. Private keys further generate the wallet's public keys, which are uniquely associated and create the wallet's key pairs.
Public Keys
Public keys, like private keys, are also a long set of alphanumeric characters and act as their wallets' recipient addresses. Anybody looking to send another user cryptocurrency directs it to the recipient's public key. When the transaction gets confirmed, the cryptocurrency gets sent to the recipient's wallet and is tied to the public key through cryptographic encryption. Looking closer, the wallet addresses that users direct funds to are often shortened versions of the long alphanumeric public keys for convenience.
The associated private key from the key pair is needed to decrypt and transact the stored funds. That is how they are paired to secure user funds on the blockchain. Security arises from how public keys are generated. Because of the asymmetric cryptography used in crypto wallets, public keys generated from private keys cannot reverse engineer the private keys. Therefore, it is only possible to access the funds in a crypto wallet by knowing its public key.
Despite that, public keys must be managed safely and kept from unrequired entities. With enough knowledge about users and their wallet public keys, bad actors can attempt phishing, malware, and social engineering attacks to obtain their private keys and steal their cryptocurrency. Inversely, they can indulge in identity theft by presenting users' public keys to third parties.
Seed Phrases

Private keys can be stored less prudently than public ones, so losing complete access to wallet addresses is far-fetched. But the same cannot be said about private keys. Because they need to be stored securely, there is a big chance of losing access to them and the cryptocurrency they are associated with.
Wallet manufacturers following certain cryptography standards incorporate seed phrases into their wallets so users can regenerate their private keys and regain access to their trapped cryptocurrency. The phrase, also known as recovery or mnemonic phrase, consists of simple words generated in a random yet specific order while users set up their wallets for the first time. The number of words in the phrase can either be twelve, eighteen, or twenty-four, depending on the manufacturer and the model of the wallet.
When the phrase is entered, the wallet taps into its master private key to regenerate its private and public key pairs as before. Seed phrases must be stored as securely as one would their private keys while simultaneously maintaining accessibility for when it is required. That includes the usage of HSM (Hardware Security Module) cold wallets, air-gapped devices, paper wallets, and storage safes.
If others access a wallet's seed phrase, they can generate its private and public key pairs and drain out the user funds associated with the pairs. Additionally, losing a wallet's seed phrase implies that the cryptocurrency will surely get stuck if the user loses the private key associated with said cryptocurrency.
Additional Security Measures

At moments, be it because of luck or cybercriminals being a step ahead; users can lose their cryptocurrency to theft even after securing their wallets adequately. As a result, certain others prefer fortifying their storage practices to the maximum degree.
They can turn to multisig (multi-signature) wallets for increased cryptocurrency users' security. In a nutshell, these wallets contain multiple private keys needed to initiate a transaction. The idea is that even if a cybercriminal gets hold of one or a few private keys, they cannot drain the wallet's funds.
They come in various combinations and work in an m-of-n configuration, where m is the minimum number of keys required to sign a transaction and n is the maximum number of keys. In certain cases, m and n can be the same, meaning all keys in the configuration are required to sign a transaction. For example, for wallet internal 2FA purposes, users can use a configuration of 2-of-2 private keys.
Otherwise, external 2FA implementations like biometrics, passwords, and pins can be used to safeguard storage devices and their contents. Using air-gapped, cold storage devices is the most secure way to store private keys. In addition, present-day HSM cold wallets come packed with additional protective layers, taking security to another level.
On the other hand, wallets on network-connected devices, called hot wallets, are prone to hacks and malware attacks. Therefore, although they are popular, they should only be used to store large amounts of cryptocurrency temporarily. Instead, they can be used to keep minuscule amounts for immediate transactions, owing to how much faster they are than cold wallets.
Risks And Vulnerabilities
Safety is always emphasized while transacting and storing cryptocurrency because of all the risks present with the asset class. Cybercriminals always search for their next victim and prey on their funds. They often use a combination of attacks against users for increased advantage but are also known to use them singly.
Phishing Attacks
An easy way scammers dupe their victims is by using phishing attacks. They set up fake websites of crypto exchanges and custodians and guide victims to malevolent sources by email or instant messaging. Scammers collect and use sensitive information when users log in to fake websites with genuine login credentials. Sometimes, scammers can get lucky enough to have users give away their private keys during phishing attempts. However, most users do not get fooled to that degree.
Social Engineering
Scammers can go even further to run away with the funds of hard-to-get users. They use social engineering methods to gain the trust of their victims. They pretend to be genuine employees of the crypto businesses that the victims use and persuade them to share critical information like private keys and seed phrases. Reasons like identity verification or wallet dysfunction are most used during such attempts. Victims who get persuaded share the information asked for and lose the cryptocurrency they hold.
Malware Attacks
Beyond phishing and social engineering, scammers also use malware attacks to snatch user funds. First, they infect user devices with malicious software that can scrape through the data present on the device. Then, in no time, scammers can detect private keys stored on devices and transfer out user funds from their wallets.
Conclusion
Cybercriminals and scammers are always at it to walk away with user funds. Although established blockchains are highly secure, how users hold and handle their wallet keys and seed phrases needs to be improved in security.
Therefore, best practices while handling crypto wallets need to be always observed. Additional security measures like the usage of multisig wallets go a long way in helping secure user cryptocurrency. So do other layers of additional security like 2FA and pin protection.
However, going overboard with several sophisticated security implementations may make retrieving the stored cryptocurrency hard or even impossible. That is truer for users unfamiliar with the measures they use to secure their funds, and learning about the architectures used to bring security before their utilization is best. The idea behind good cryptocurrency storage practices is to balance security with ease of use.