White Hat Hackers: Who Are They, And Why Do We Need Them?

The ability to bring business online is one of the most crucial benefits of the internet to trade and commerce today. Websites, applications, and software are making life convenient for all. With the massive number of people using the internet for various purposes, a lot of money and data flow through all the infrastructure built on the web. Because of all this value, bad actors look to use nefarious means to steal and extort funds from users and businesses.
Companies from all industries, big or small, are prone to cyberattacks, more commonly referenced as hacks. The people behind them, called hackers, are more widely known to cause severe damage to the reputation and finances of companies. Such exploits are quite common in the fintech space and more so with blockchain and DeFi, where they are reported frequently. However, the term hacker is broader than just bad actors and includes good actors, also known as white hat hackers.
Who Are White Hat Hackers?
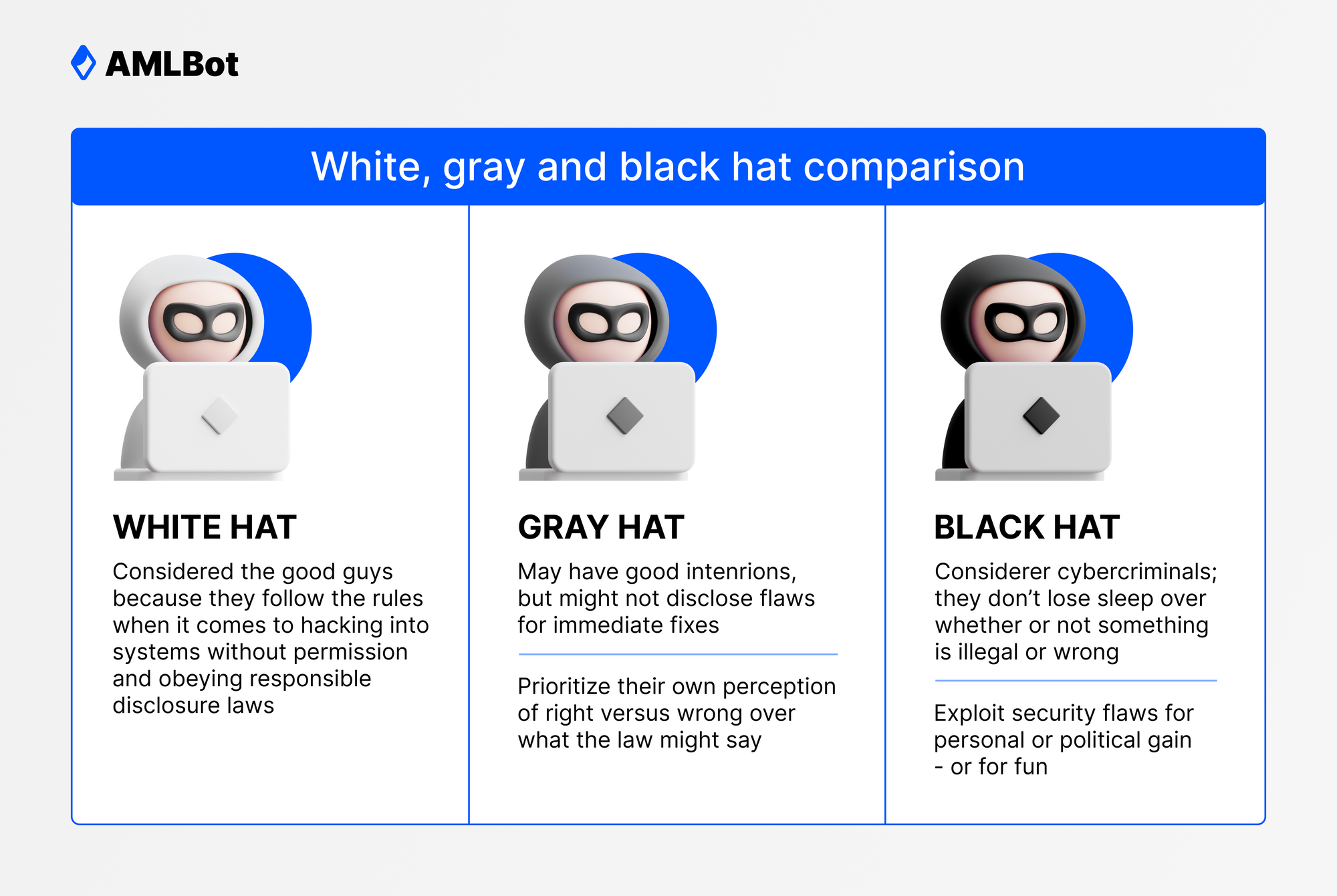
White hat hackers are the good guys when it comes to hacking. They are like any other hacker who can break into applications and web systems but use their abilities for ethical purposes. Companies hire them to find vulnerabilities in their infrastructure. By doing so, companies could save huge amounts of money and reputation by patching pitfalls in the platform’s security that other nefarious hackers could have attacked.
Ideally, a company’s cybersecurity measures should include rigorous audits and testing, which white hack hackers carry out. White hat hackers, therefore, hack into company systems, exploit vulnerabilities and deploy social engineering methods on employees with the company's permission. Thus, they help build robust infrastructures for companies and protect their brand, resources, and operations.
The Other Type Of Hackers
The word hack is synonymous with criminal activity on the web leading to unauthorized access to funds and data. While we have discussed the brighter side of hacking, the other kinds of hackers range from ethically questionable to those involved in criminal activities that plague users and companies online. Depending on their motives, they are classified into gray hat and black hat hackers, but they both gain access to company systems unethically.
Gray Hat Hackers
Somewhere beyond white hat hackers, gray hat hackers are their unethical counterparts and do what they do to expose the flaws present in the cybersecurity measures of companies. They do so to bring it to the company’s awareness. While they are not known to hijack funds or data to profit illicitly, their activities are still murky simply because they hack companies without permission. Hence, gray hat hacking can be illegal as hackers can end up treading on local company infrastructure.
Of course, gray hat hackers are less nefarious than black hat hackers – those involved in a criminal activity whose ethics are skewed to the maximum degree. Instead, they are on a similar mission to that of the white hat hackers minus the permission to do so, raising red flags about their ethics. Gray hat hackers look at their work as a method to bring awareness to companies about their lacking cybersecurity, regardless. Some can request money to find vulnerabilities or for offering to fix them.
Black Hat Hackers
Black hat hackers are criminal entities operating in the shadows of the web to leverage the vulnerabilities present in applications and platforms for personal gain. What they do is highly unethical and, in all cases, unlawful. By exploiting software bugs, using social engineering, and many other methods, they gain access to restricted resources and systems.
Black hat hackers are known to extract ransoms once they take over company infrastructure and when they obtain sensitive information. Fintech companies are highly targeted as they deal with large amounts of funds, and exploiting vulnerabilities can mean huge paydays to hackers. The cryptocurrency sphere is loaded with black hat hackers looking to take advantage of vulnerable users and weak application infrastructure. The nascency of this space and the lack of security audits conducted by white hat hackers and other cybersecurity experts make it a cakewalk for black hat hackers to run away with stolen funds.
Why Crypto Projects Need White Hat Hackers
Blockchain protocols like Bitcoin and many more that have their fundamentals right are extremely secure from hacks. Ergo, blockchain technology is touted to be a great framework for transaction and data integrity. The issue, however, persists with the applications built on top of these networks. Wallets, dApps, and other smart contract implementations are often exploited by black hat hackers. The lack of cybersecurity audits is a concerning issue in the crypto sphere. Black hat hackers can manipulate smart contracts to their will because of the bugs present in them, so the biggest exploits in the crypto world are because of this. Look at the not-so-distant Ronin Chain and Poly Network attacks, where funds were extracted from the smart contract platforms in sums of over $600 Million in both cases.
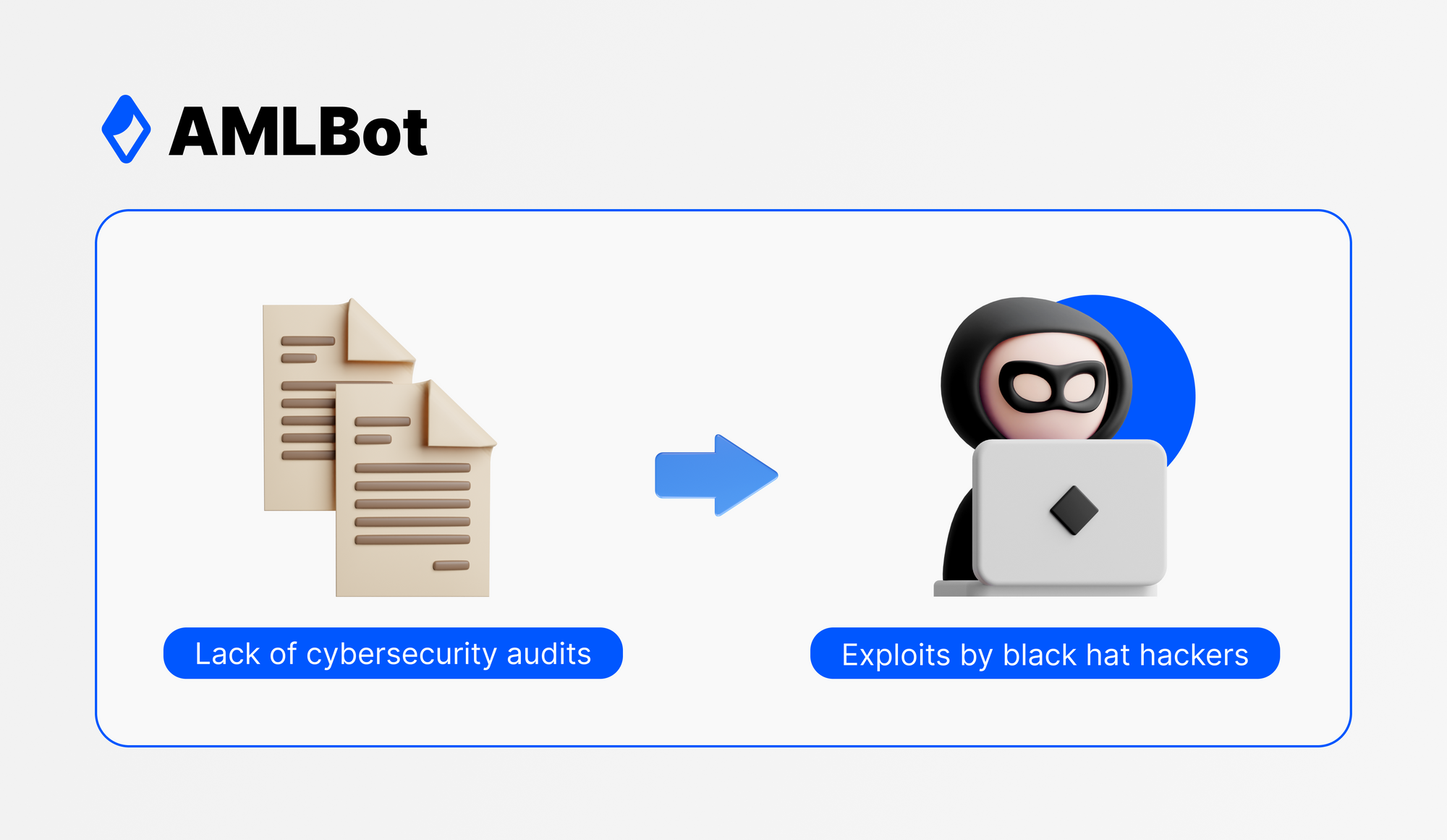
Frequent audits can prevent such attacks by black hat hackers in the crypto space. Their expertise in finding flaws in crypto project security is the need of the hour. With cybersecurity exploits only rising every year, crypto investors are losing their valuable funds, and it is promoting a bad image of cryptocurrency, blockchain, and web3 despite the obvious upsides. Through services like audits at protocol and application levels, penetration testing, and bug bounties, white hat hackers can bring a robust ecosystem where users can invest and use crypto without worries. But first, crypto projects must realize the importance of white hat hackers, as cybercriminals are constantly looking for their next exploit.